Screenshot tutorial to use OPNsense for a Reverse Proxy using multiple domains with splitdns
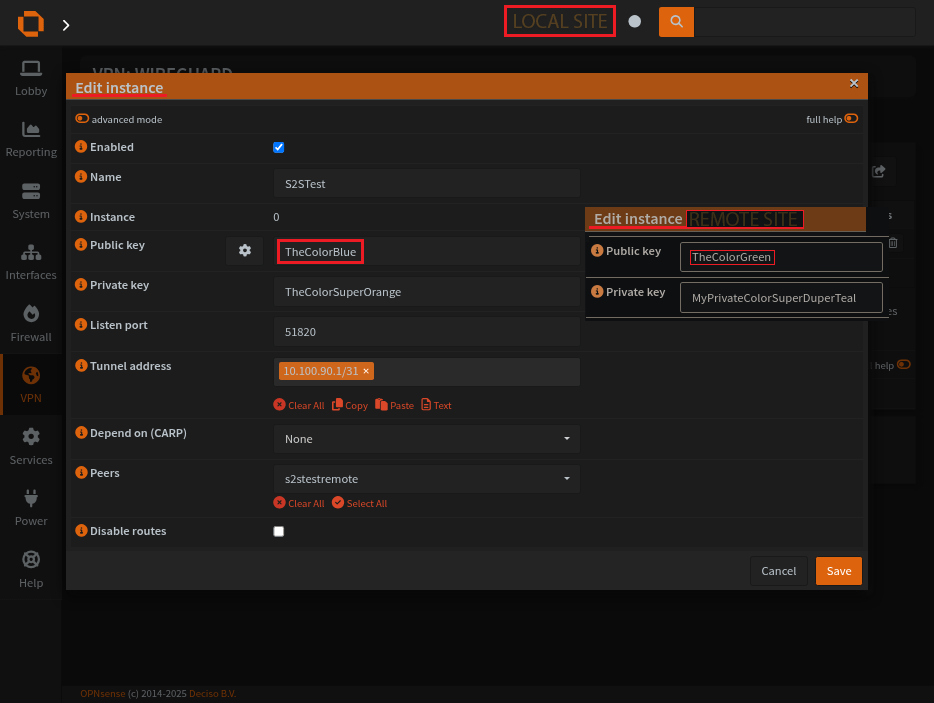
REMOTE LOCATION
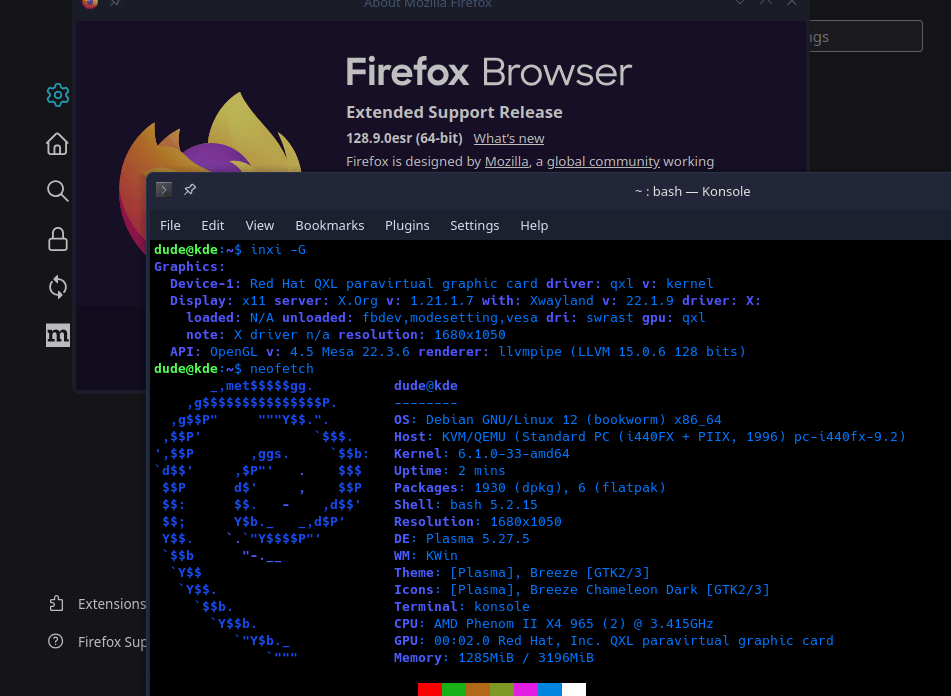
What is the current system these screen shots are from?
I am using two different desktops/browsers/systems but the same OPNsense between them.
Linux system screenshots
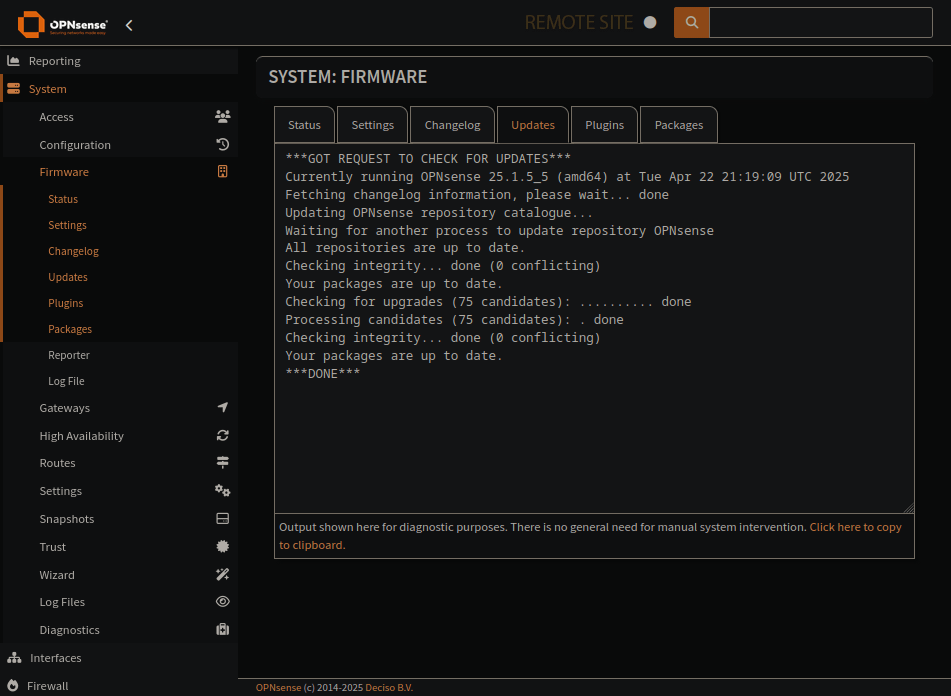
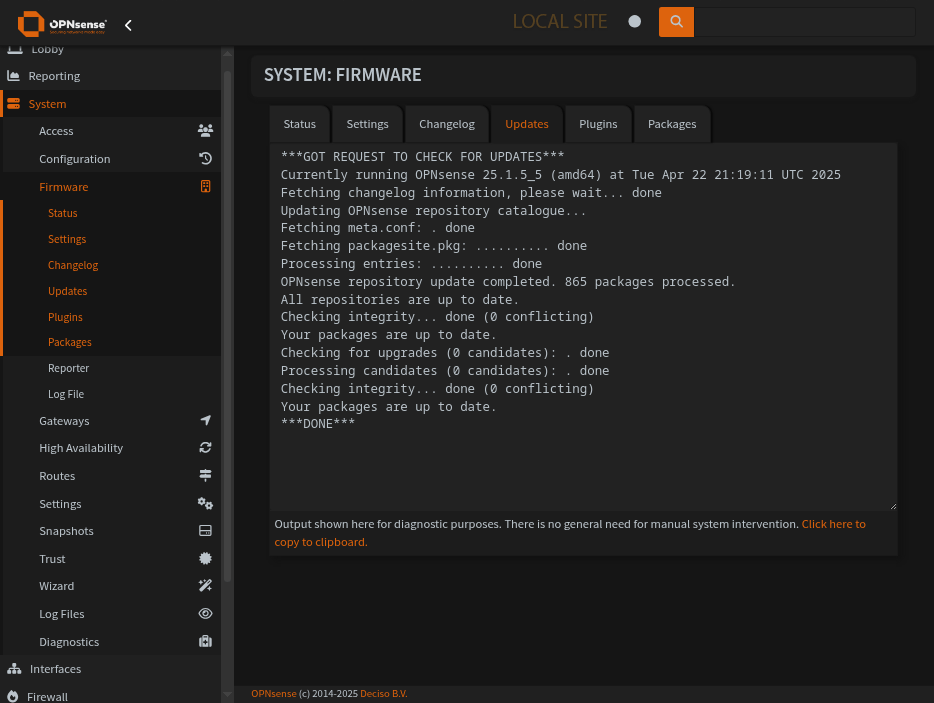
OPNSense version screenshot
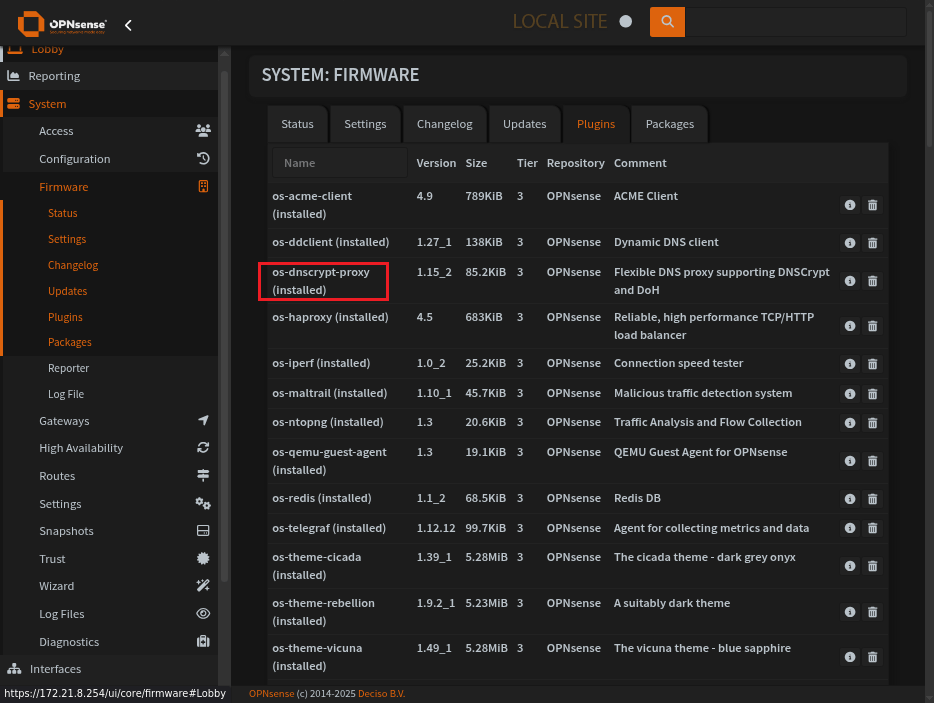
DNSCrypt-Proxy Install
This is a screen shot of the installer page.
os-dnscrypt-proxy installed
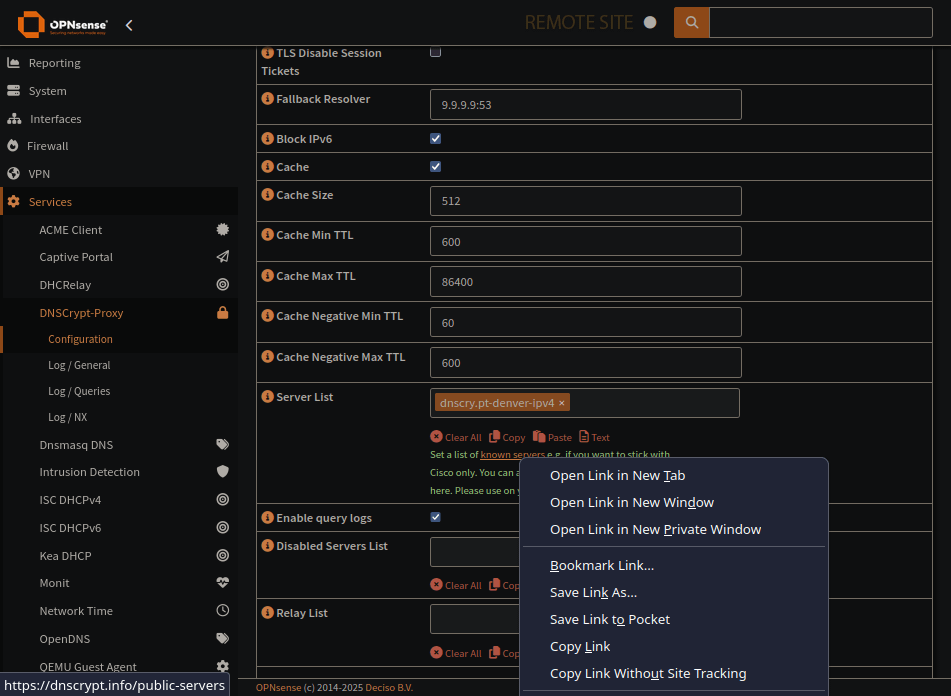
DNSCrypt-Proxy pick a server
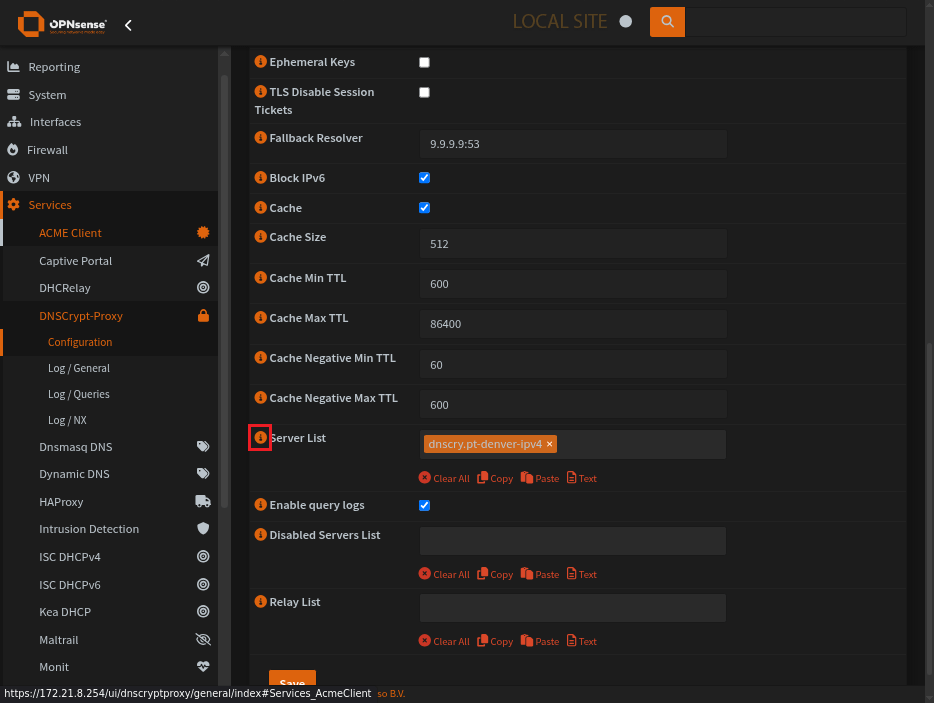
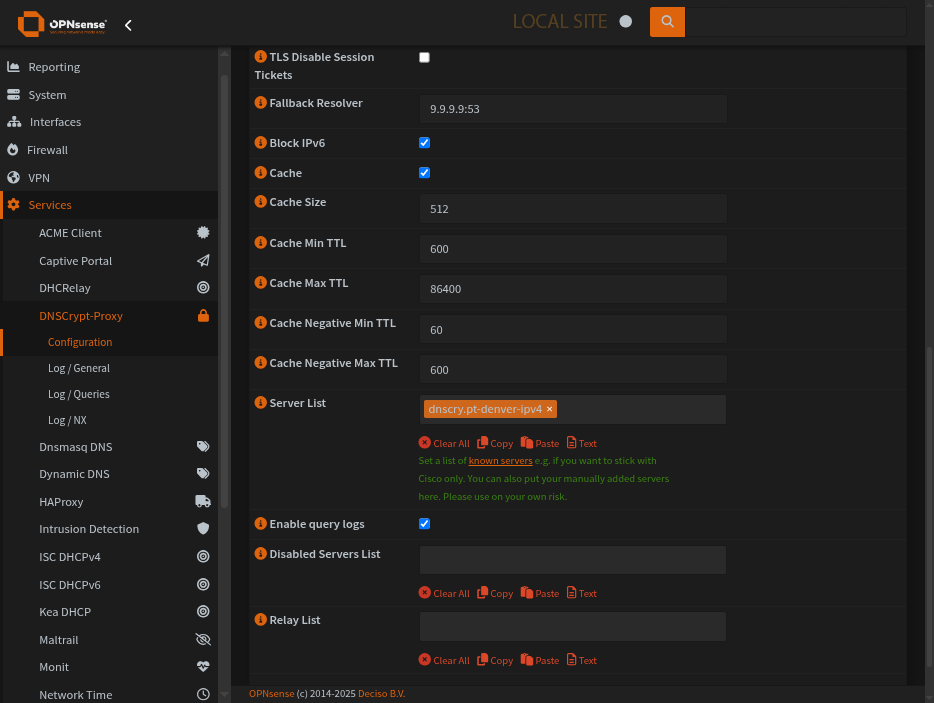
This is the main configuration of DNSCrypt-Proxy.
Enable DNSCrypt-Proxy and provide a listen address
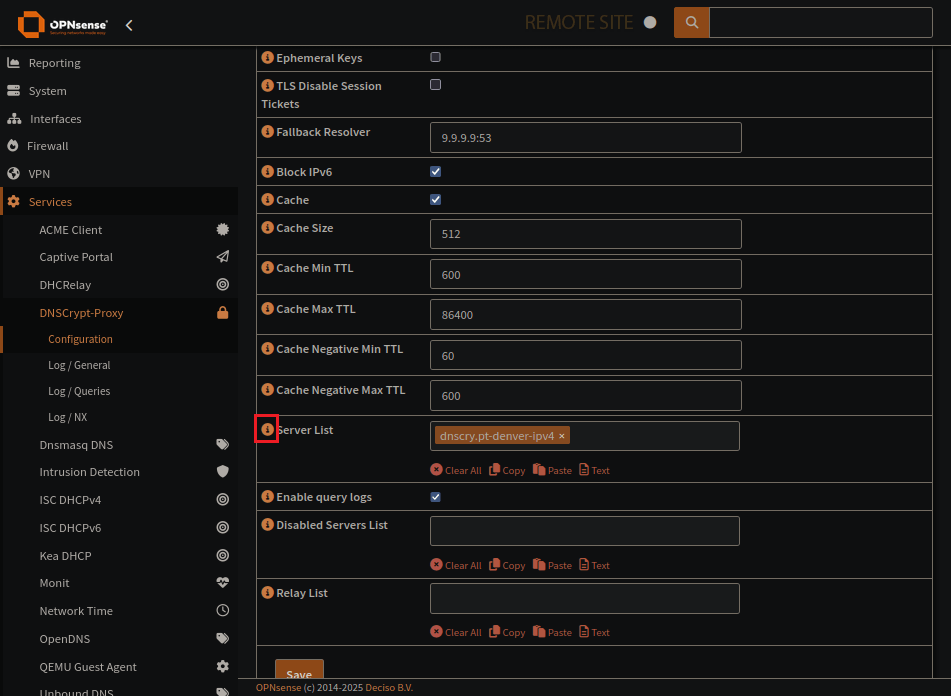
Click the ‘i’ icon to reveal the server list
Known Server list can be found in the help for Server List
Open this in a new page to pick a server
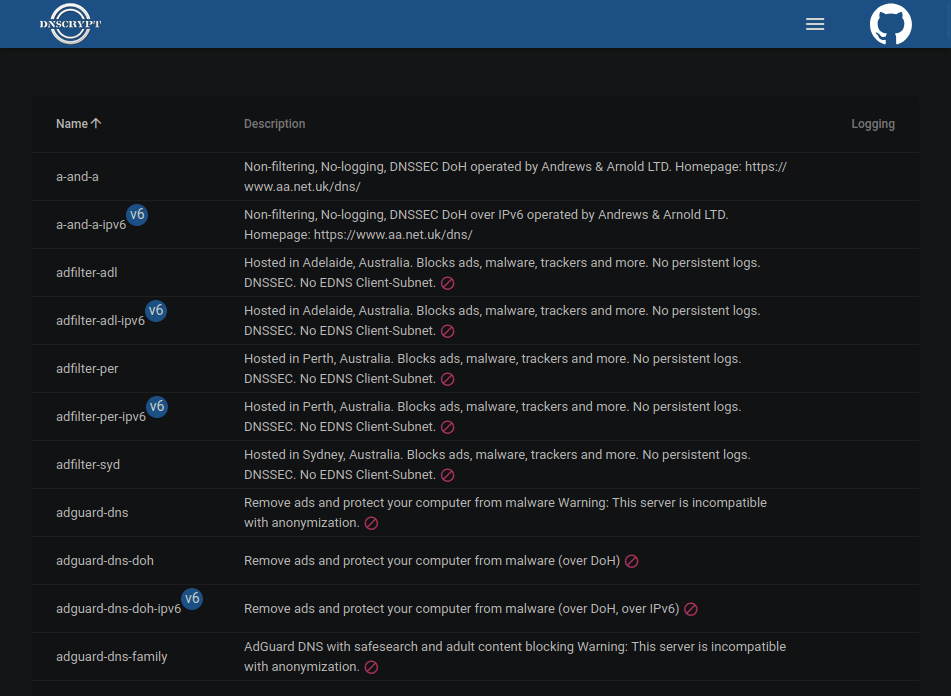
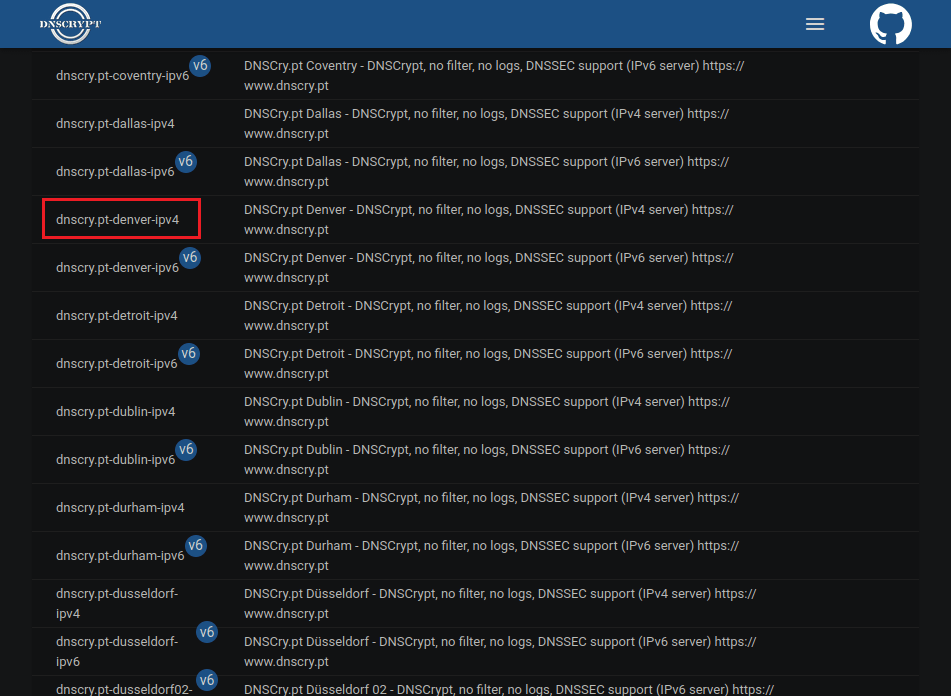
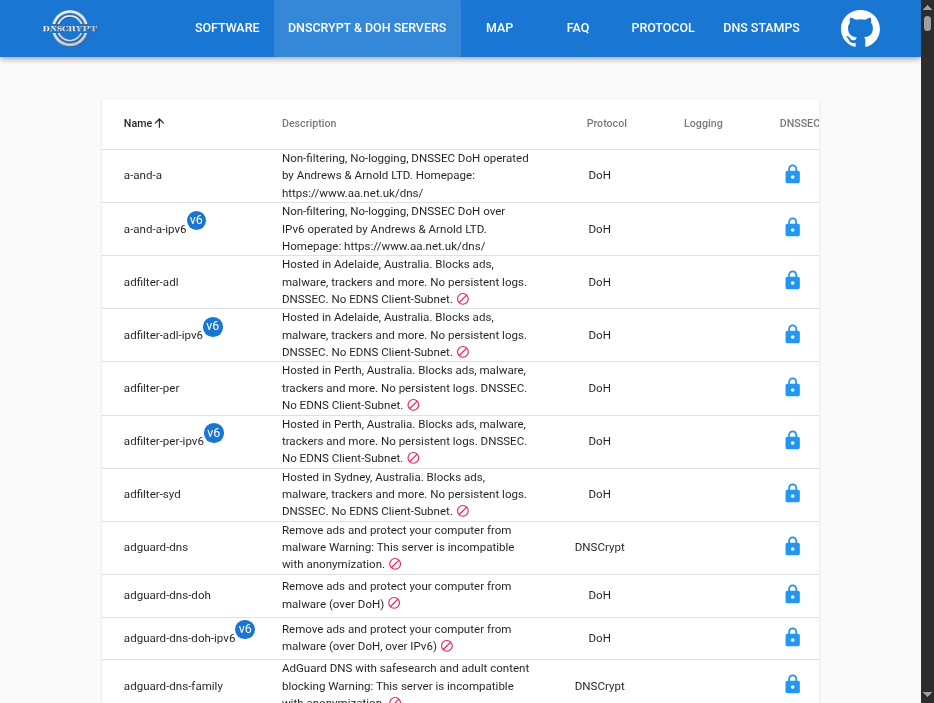
This is a demonstration of the list of servers available for DNSCrypt.
Pick one to meet your needs
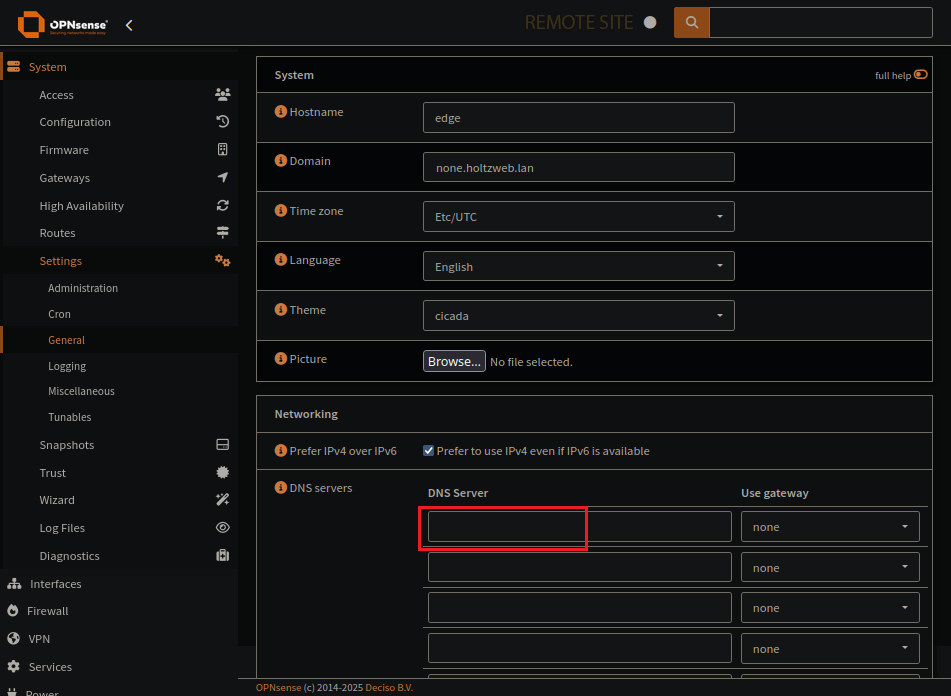
Clear and previous DNS
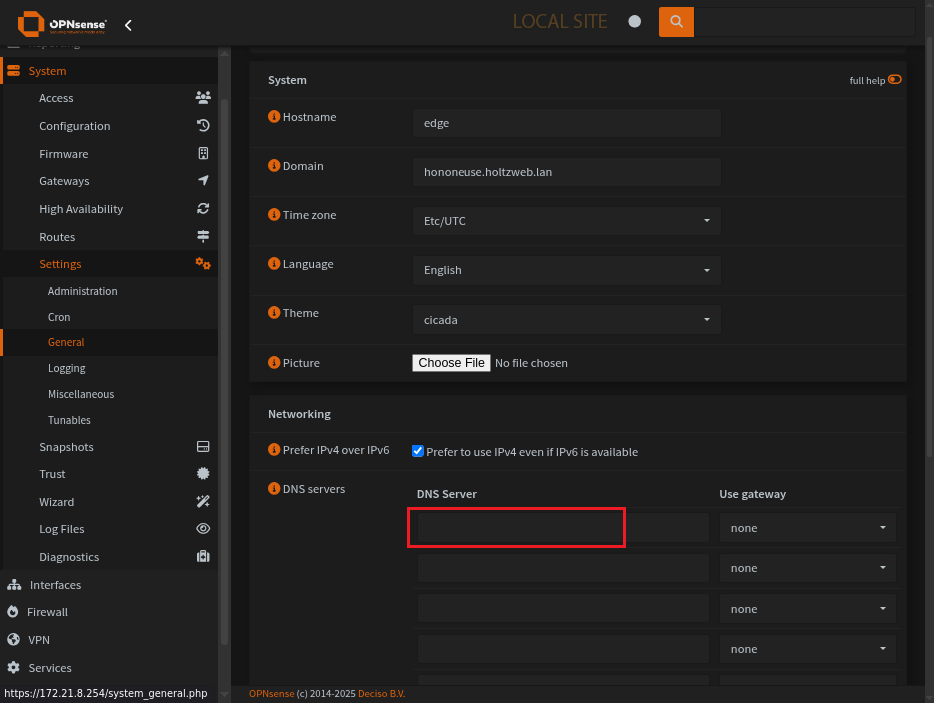
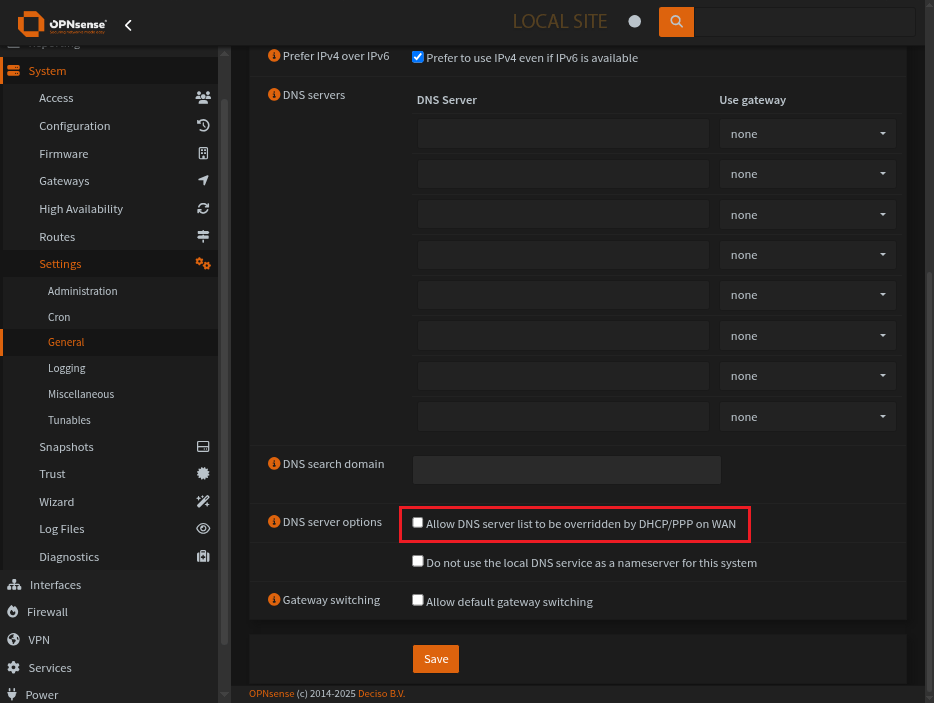
To use our new DNS server we want to be sure any previous DNS entries have been removed or disabled.
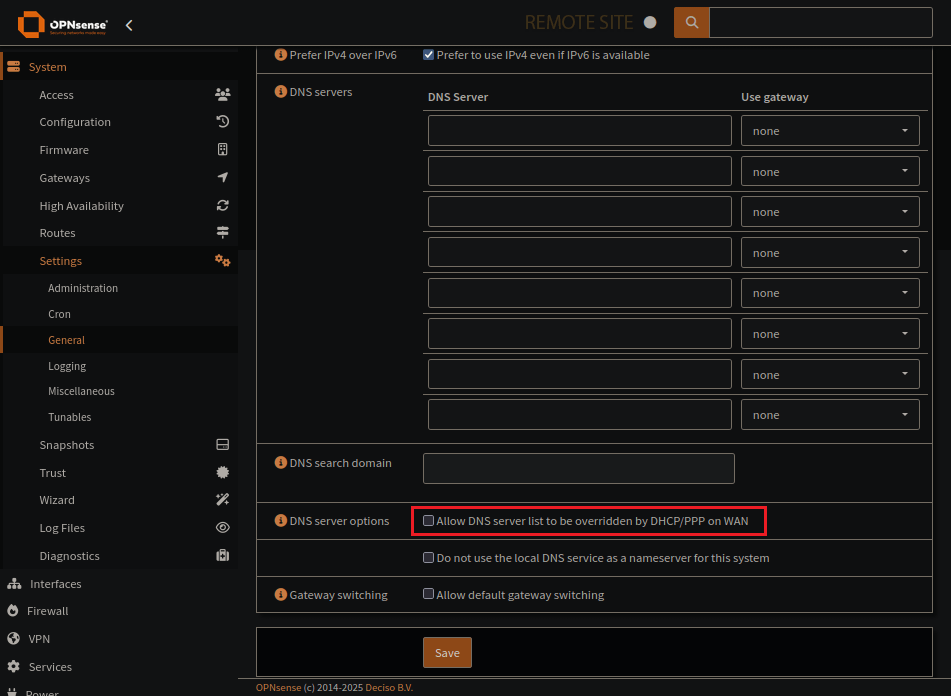
No DNS servers in the general settings
Dont allow WAN to set DNS settings
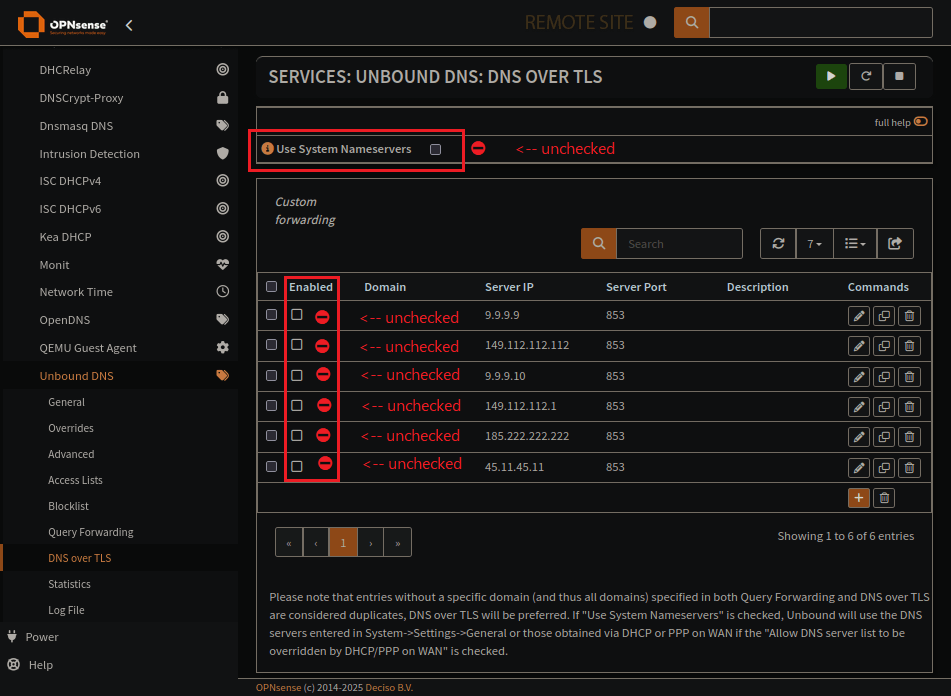
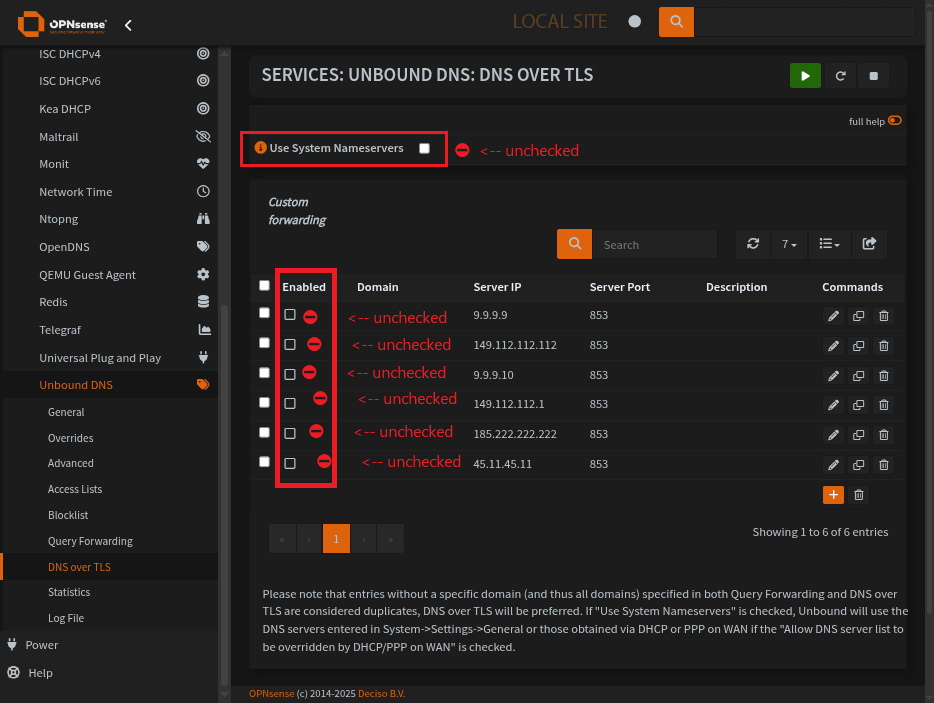
If you have DNS servers in Unbound’s DNS over TLS, be sure they are not Enabled.
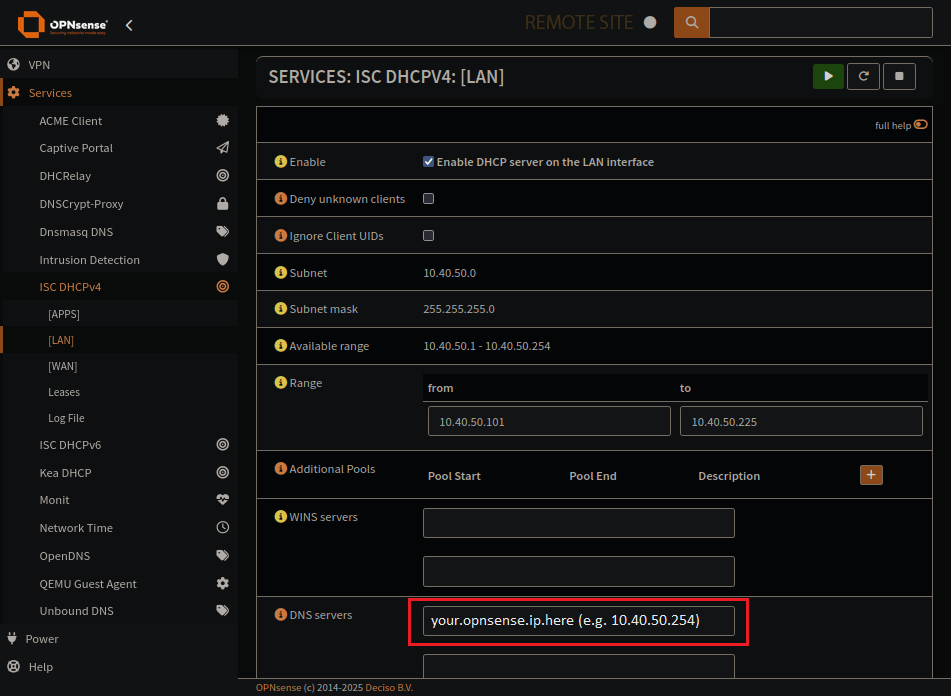
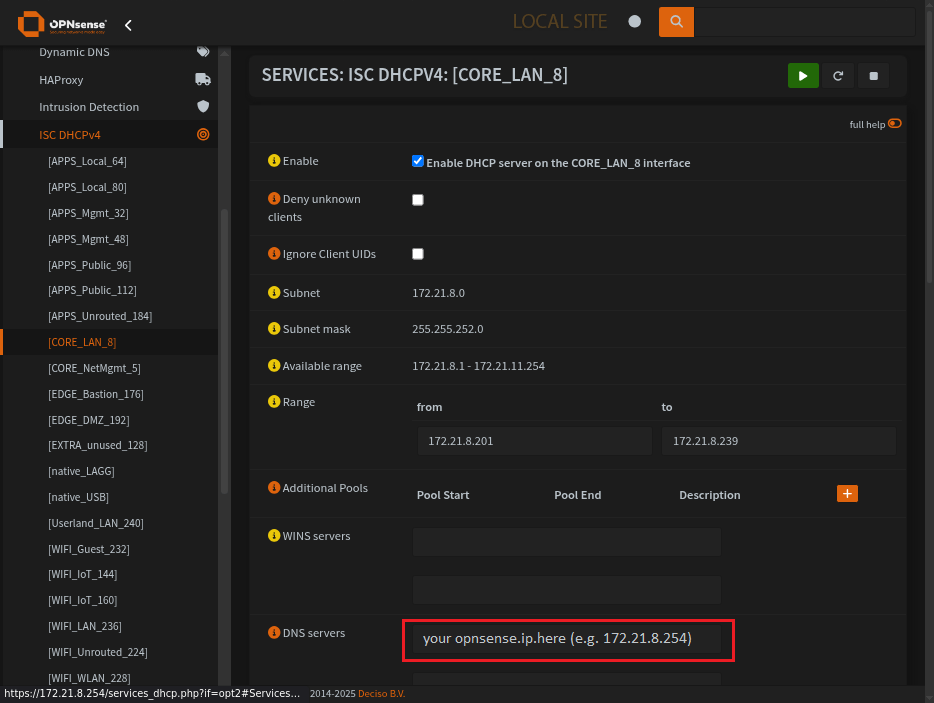
Make sure your upstream DNS server is OPNsense
You can set this to your PiHole if you like, or your Zentyal server.
But make sure their upstream DNS is going to be OPNsense. Dont let them just jet out to the root for domain lookups.
Setting up Unbound
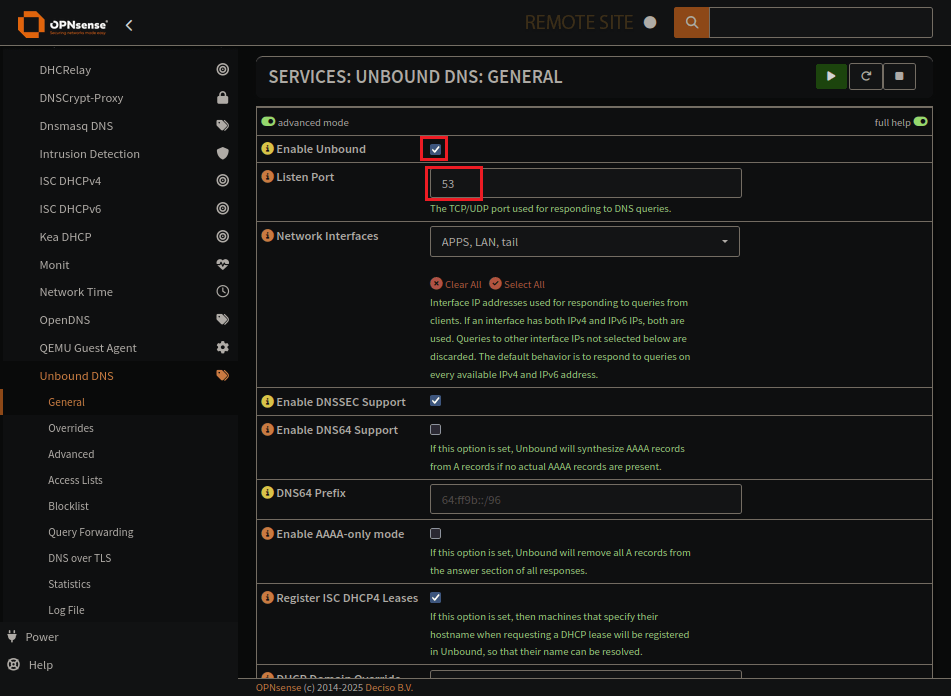
Unbound will still be the primary DNS provider for OPNsense, we just need to make some changes.
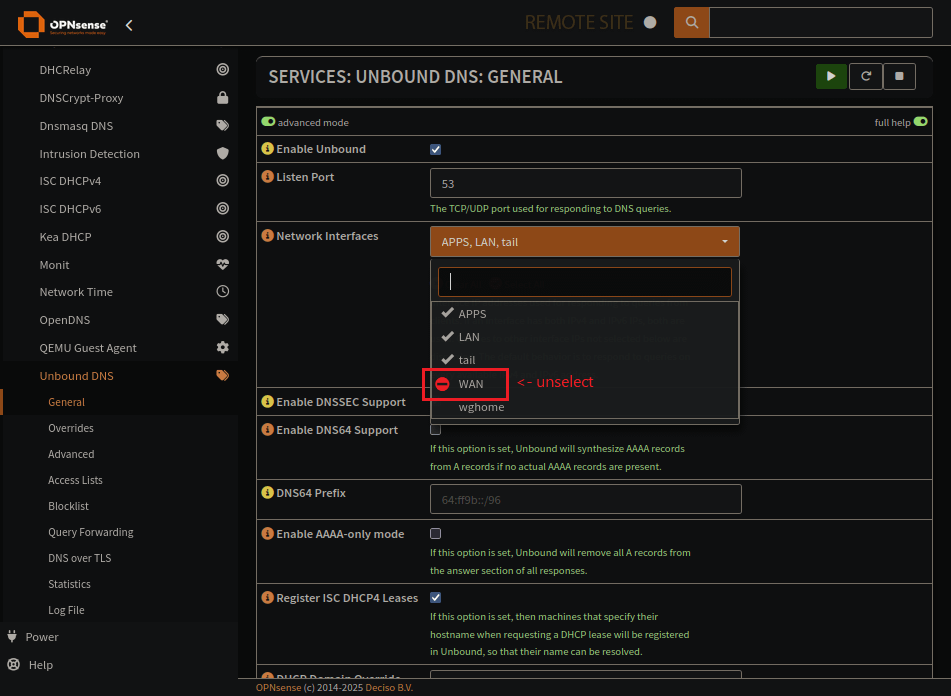
Enable Unbound and use standard DNS port
Dont set your Network Interface to WAN. Remove that.
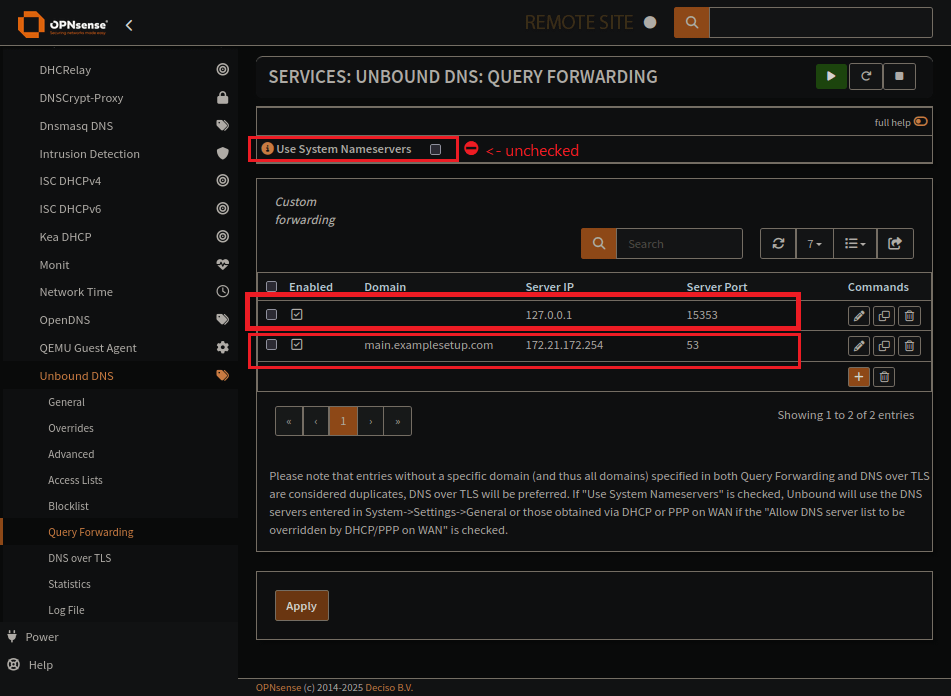
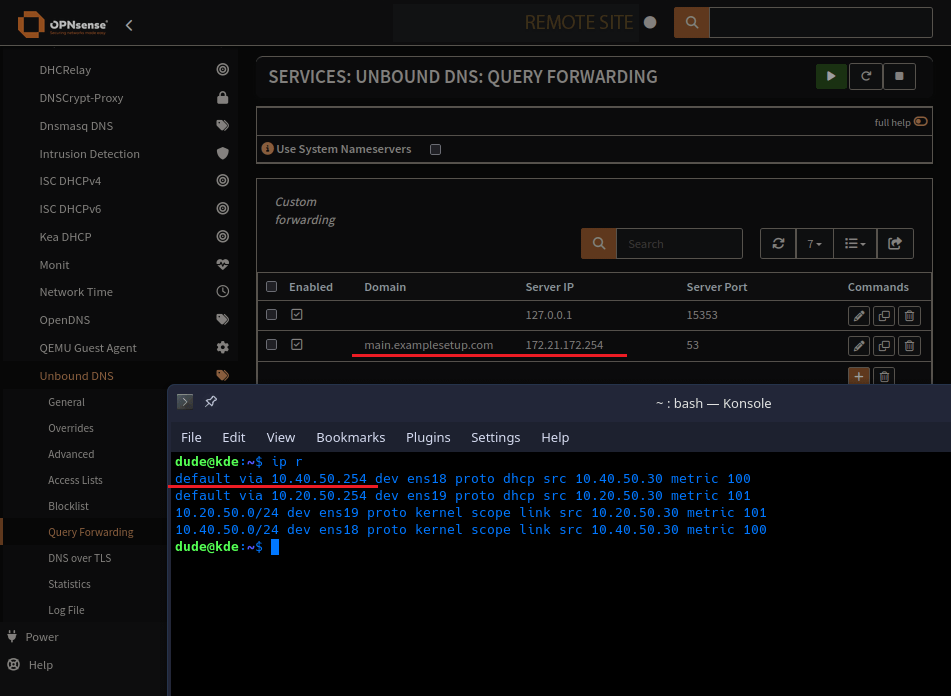
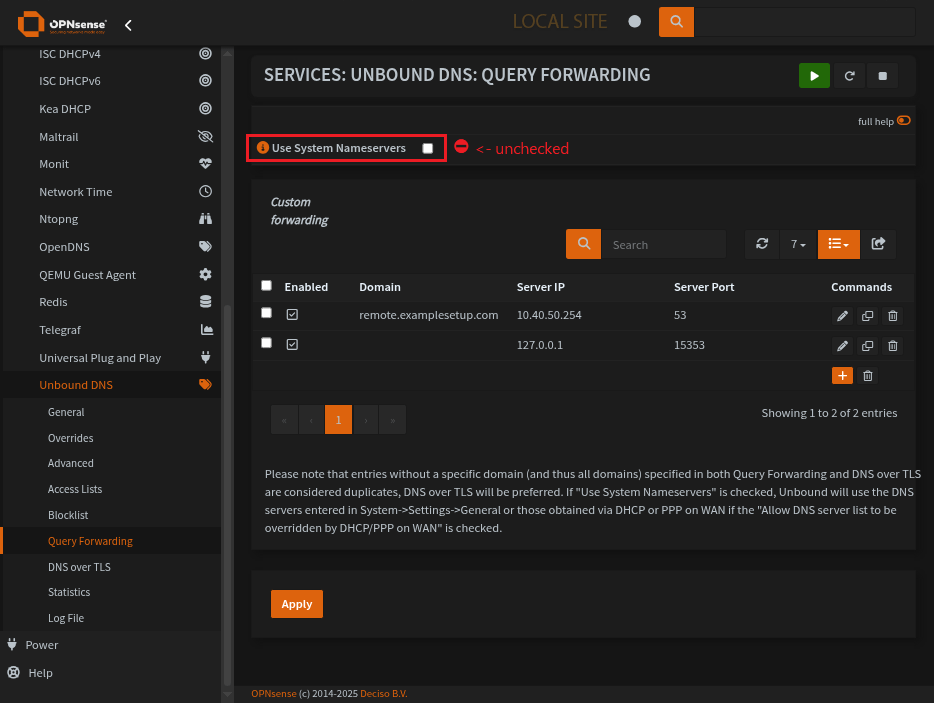
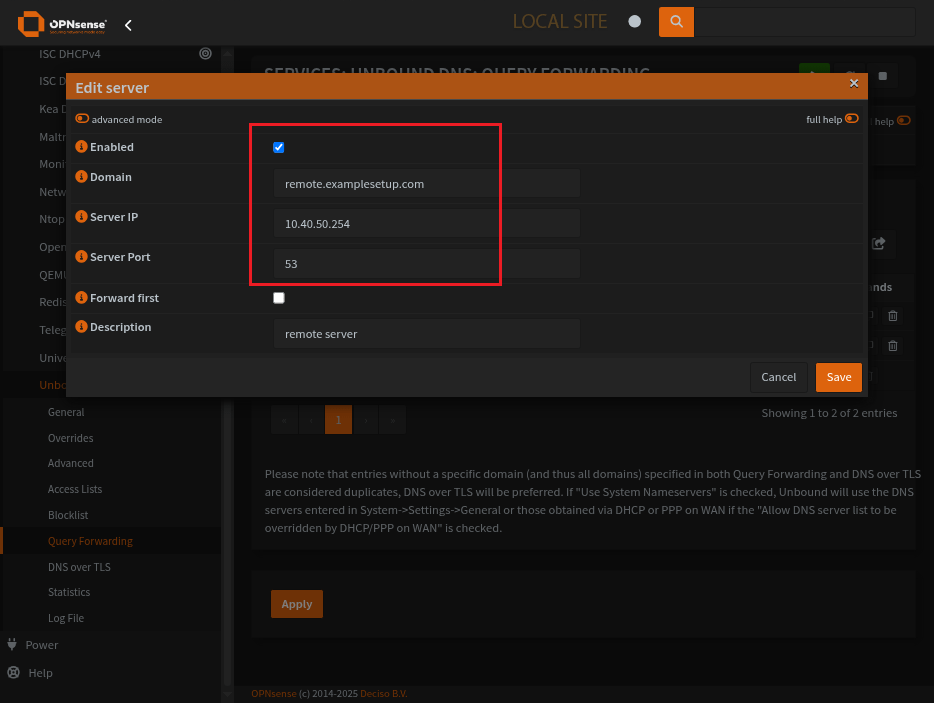
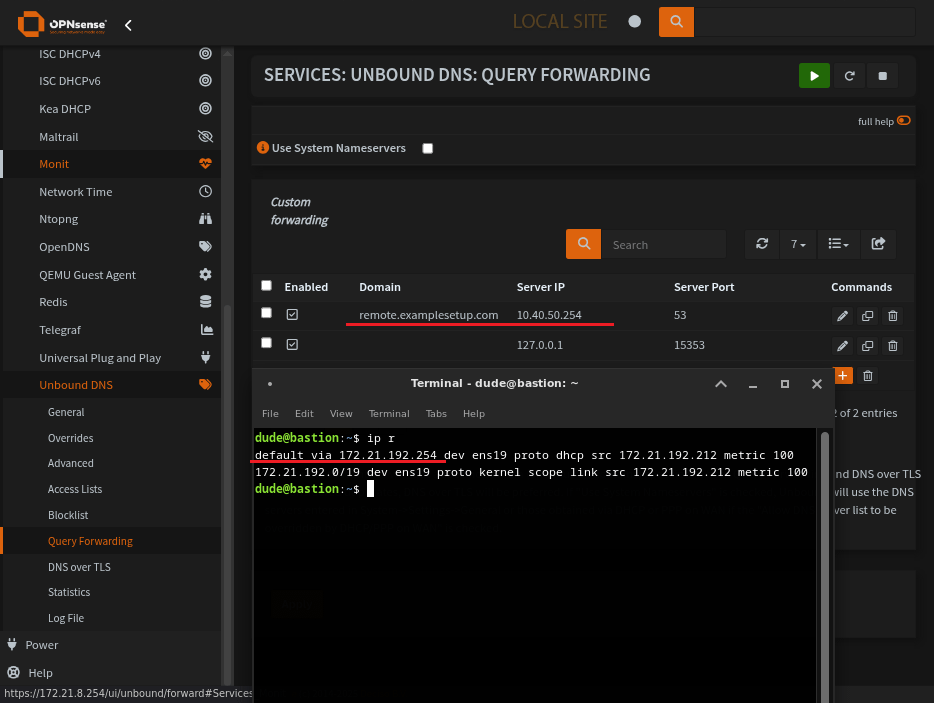
Query Forwarding with Unbound
Set the remote resolver with the domain to resolve, set the local resolver (DNSCrypt) and demo that the server ip is on a remote network. Not within our routes.
This is the main page for Query Forwarding on Unbound
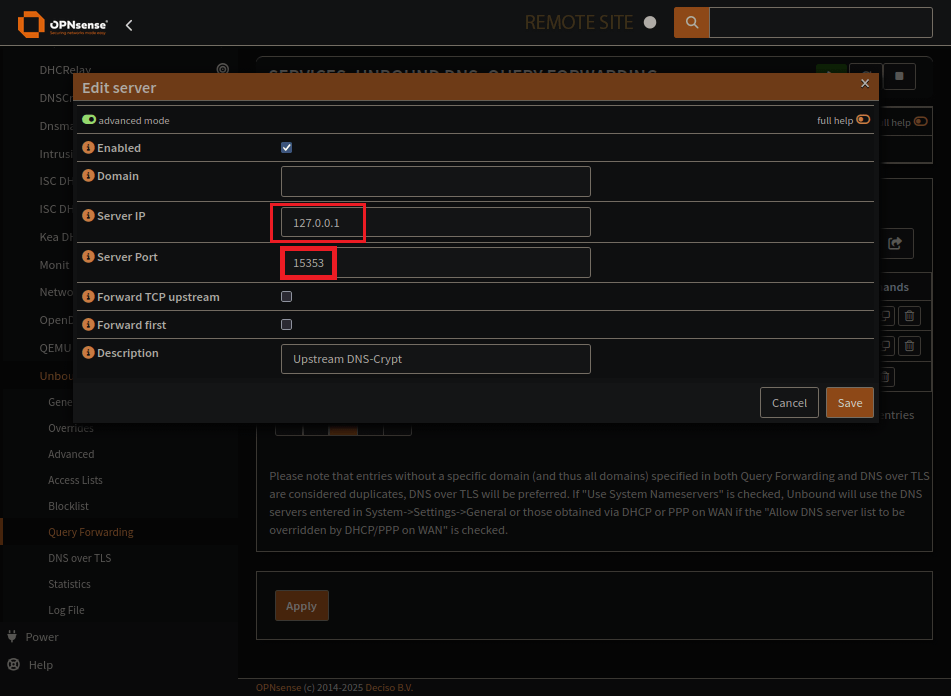
Add a new Server for DNSCrypt
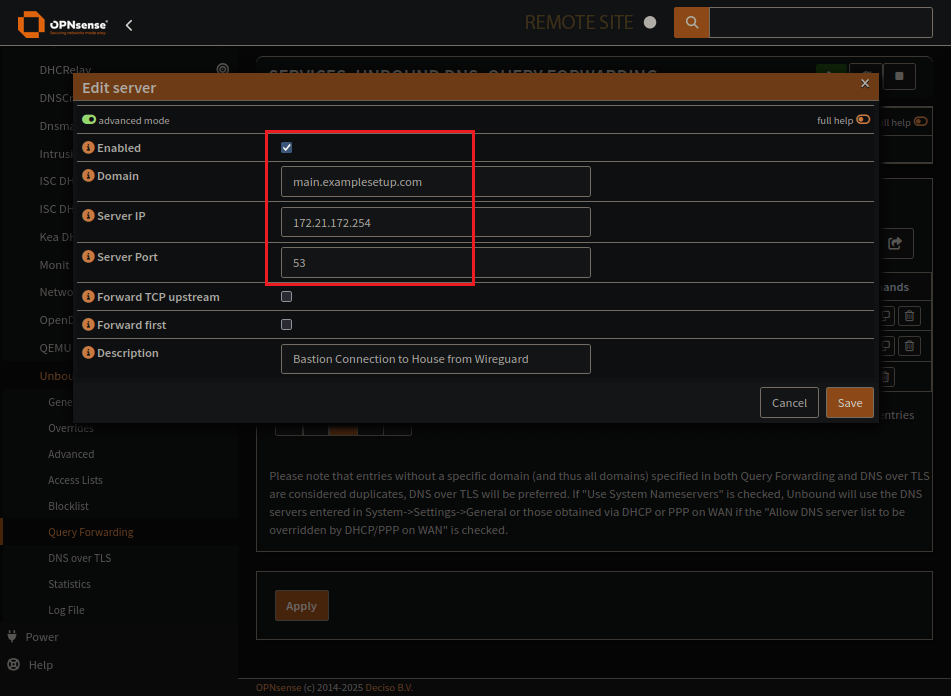
Add an entry for any remote domains and corresponding DNS server
Looks like that Query Forwarding server is a remote server
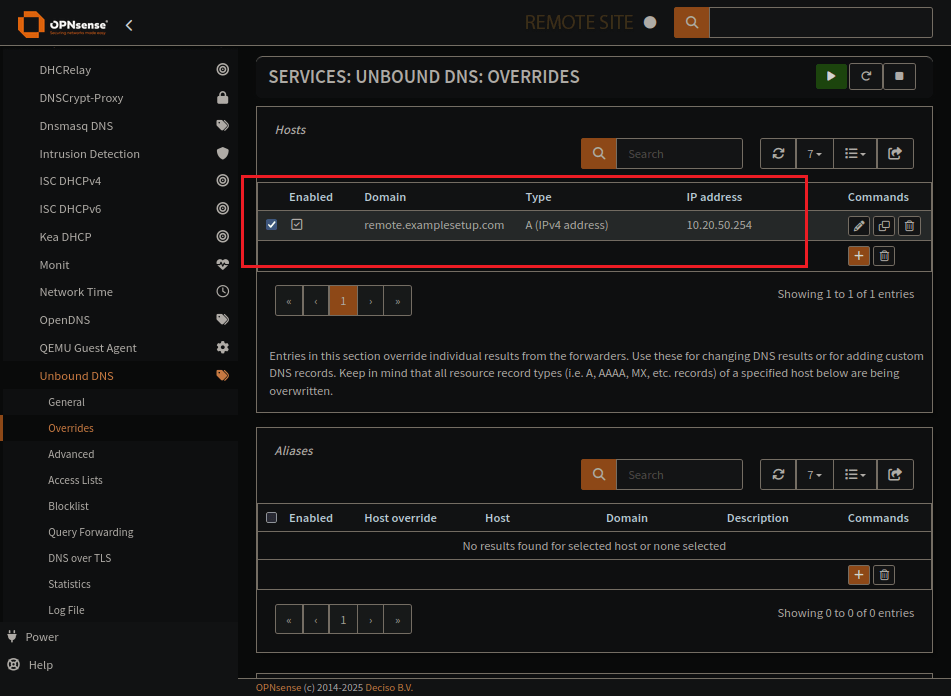
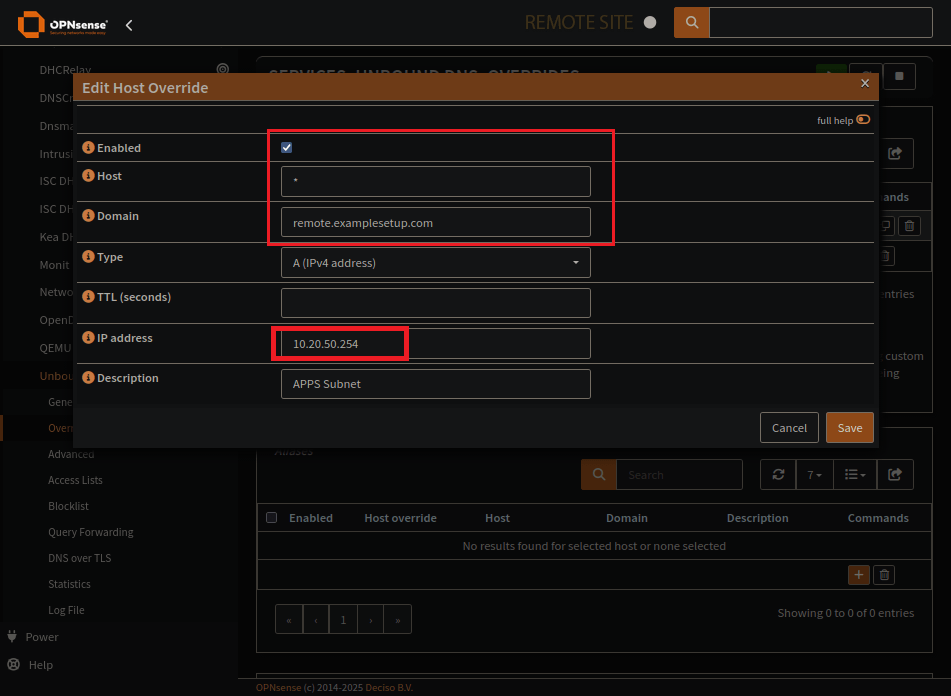
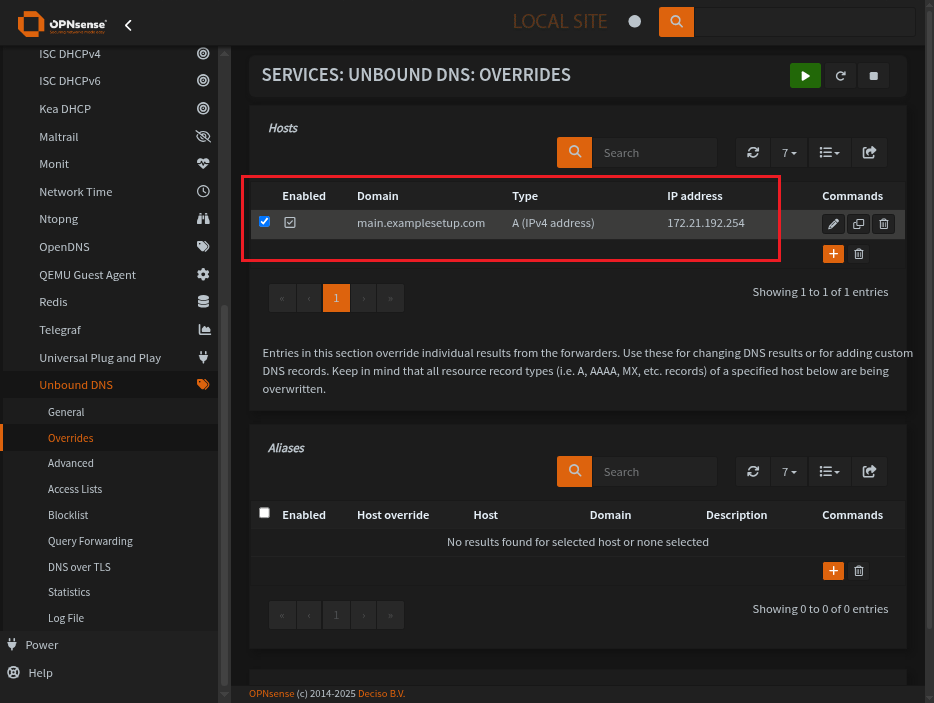
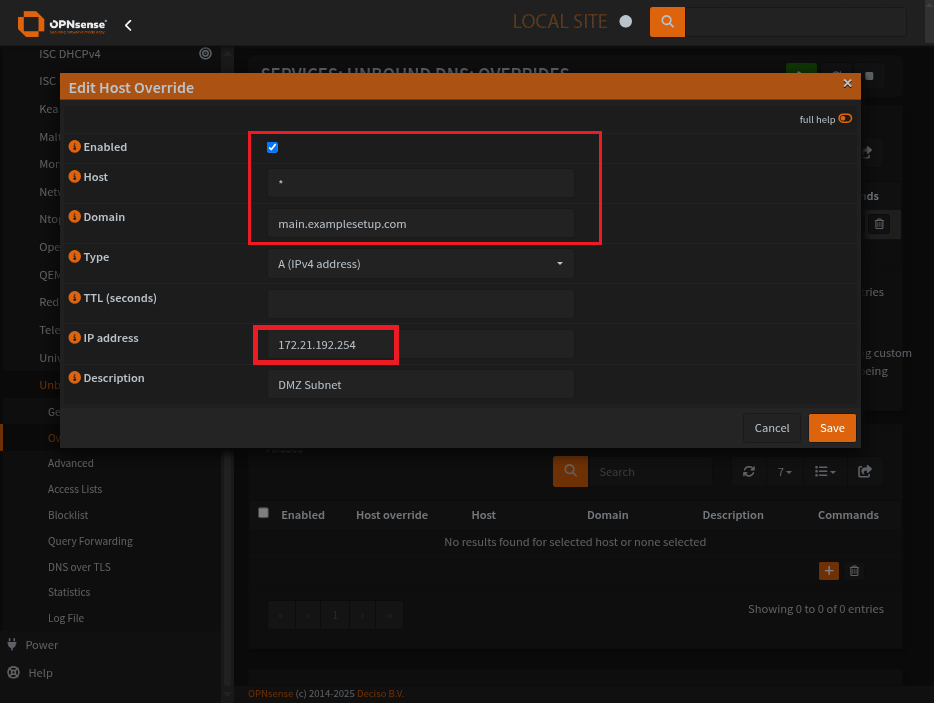
Unbound local domain overrides
These are the domains on your network. No remote servers here. Be sure to list the IP Address as the HAProxy connection you want to make, if using a virtual IP or if just applying it to an interface on an OPNsense subnet.
This is the Unbound overrides page
Setup a domain override for to a local address
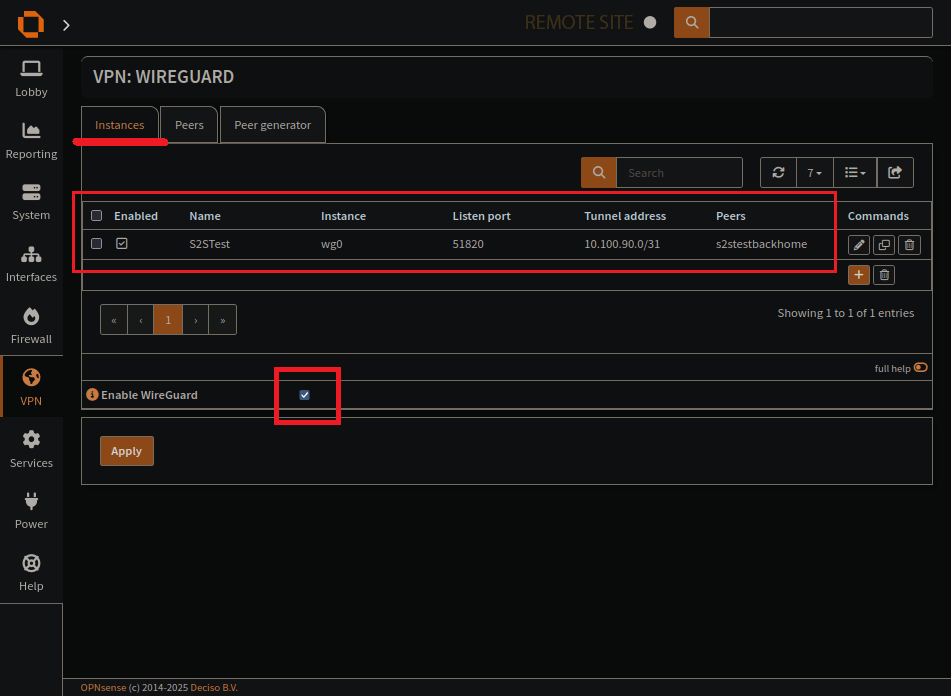
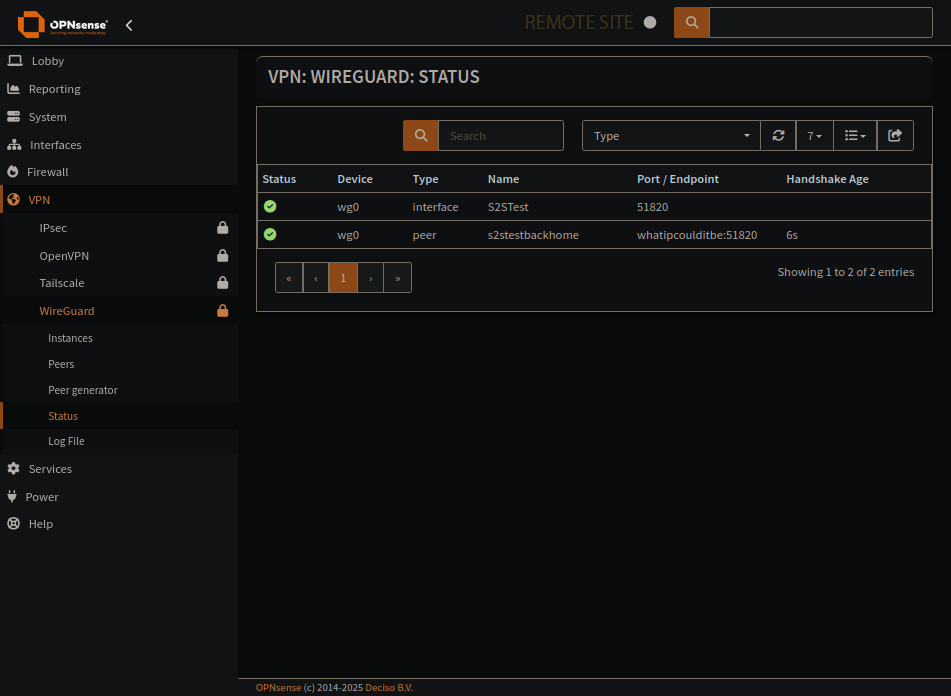
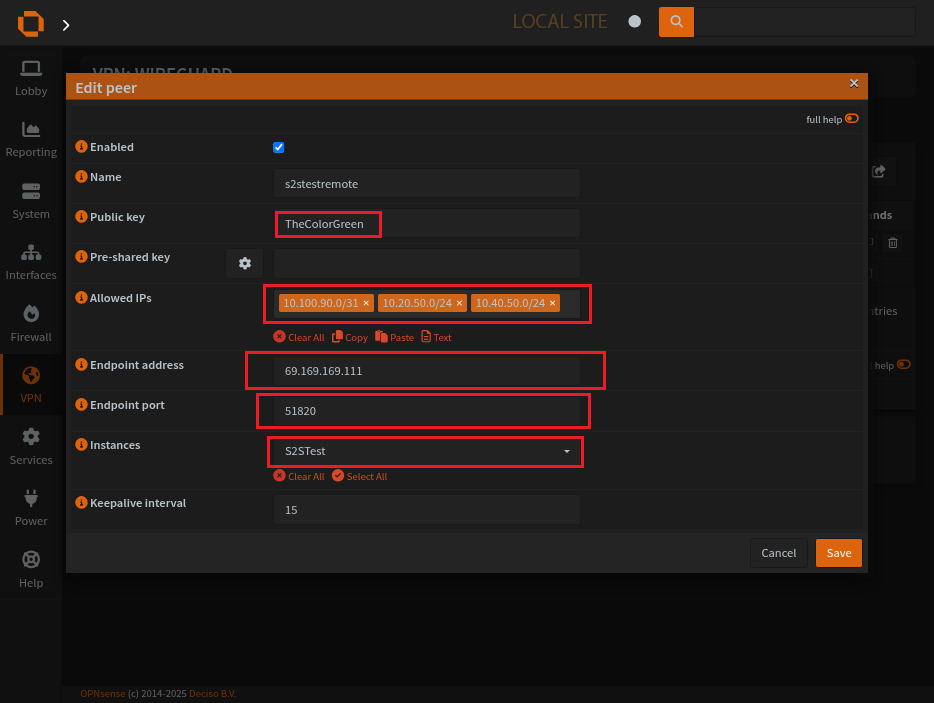
Wireguard
Quick example setup of my Wireguard:
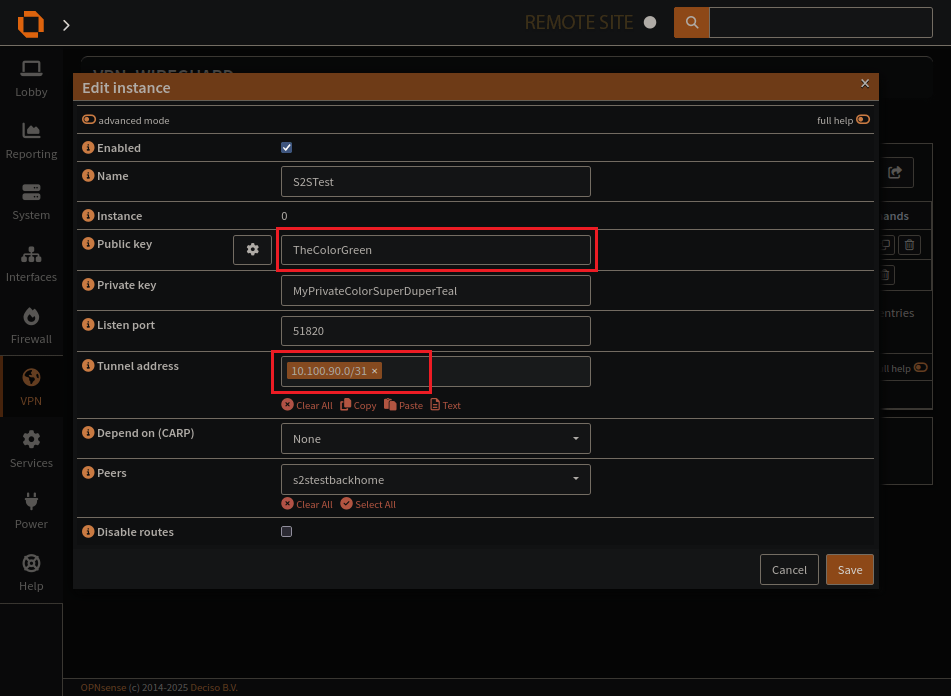
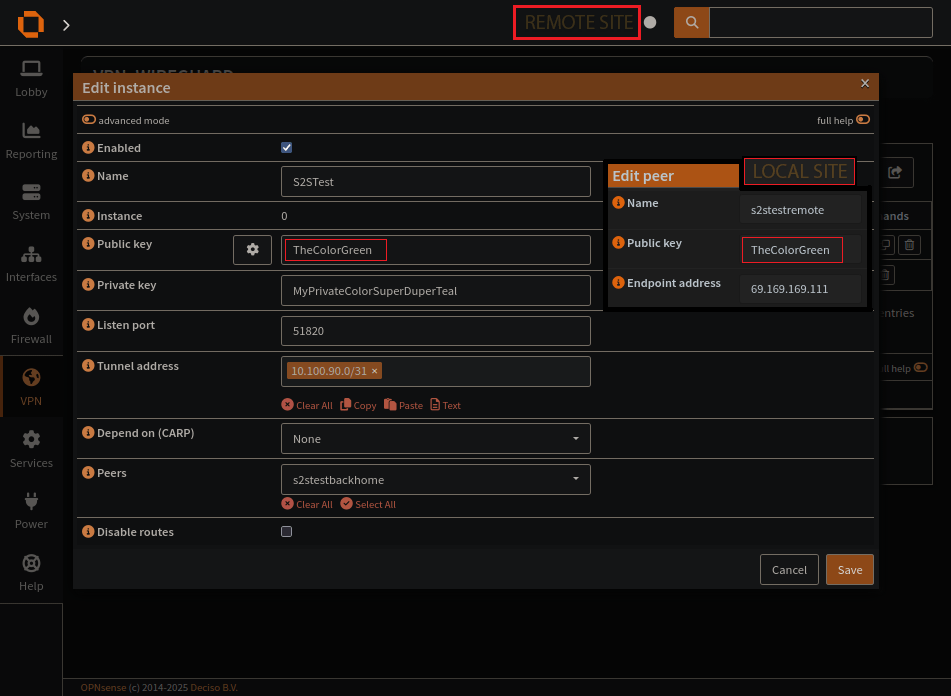
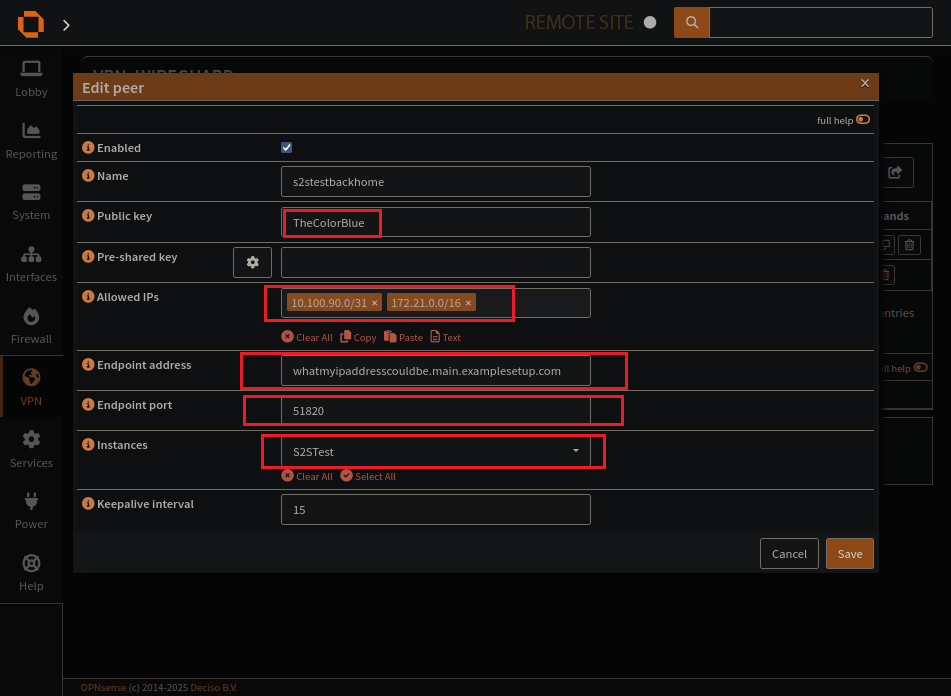
Endpoint Addresses
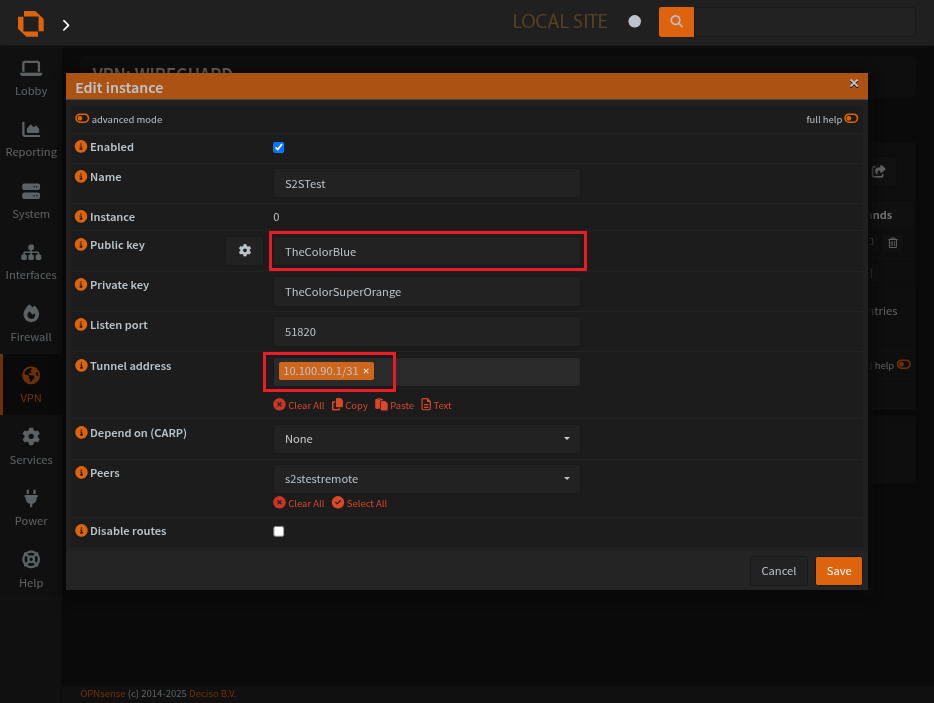
Public Key
Allowed IPs
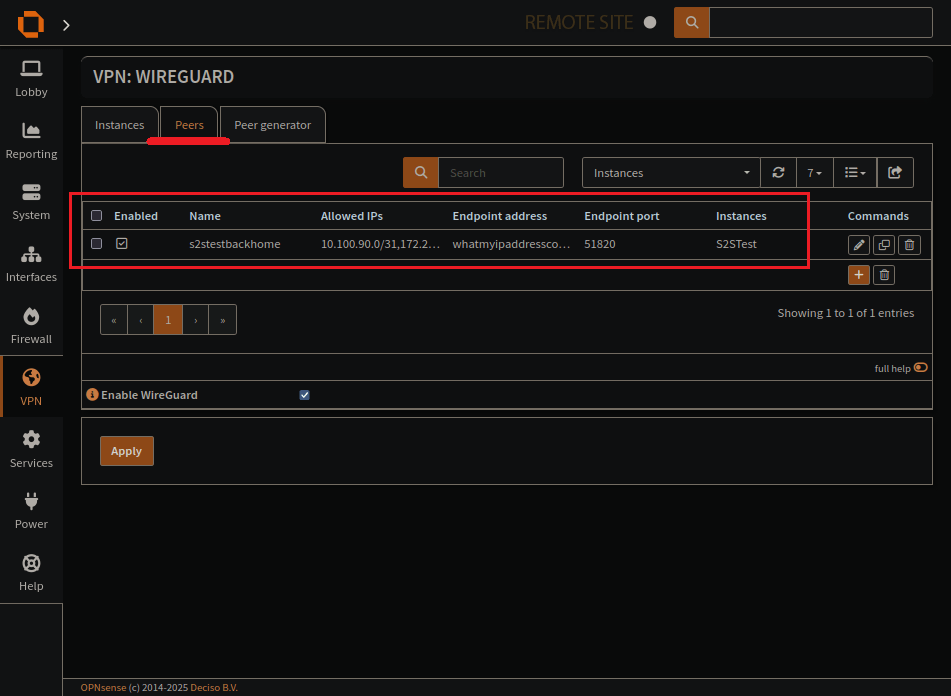
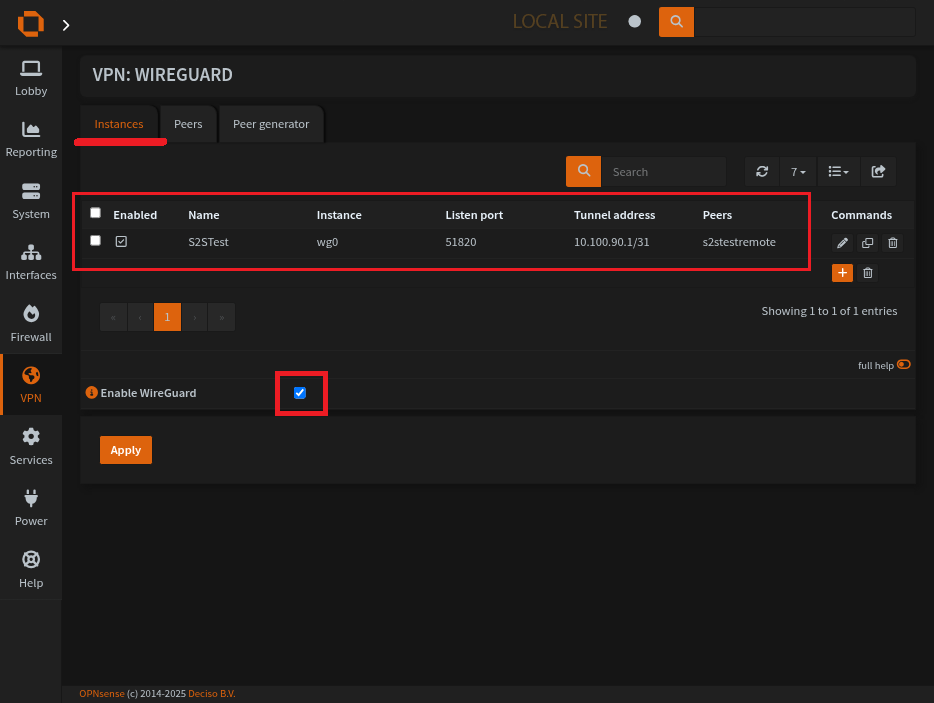
The wireguard instance page
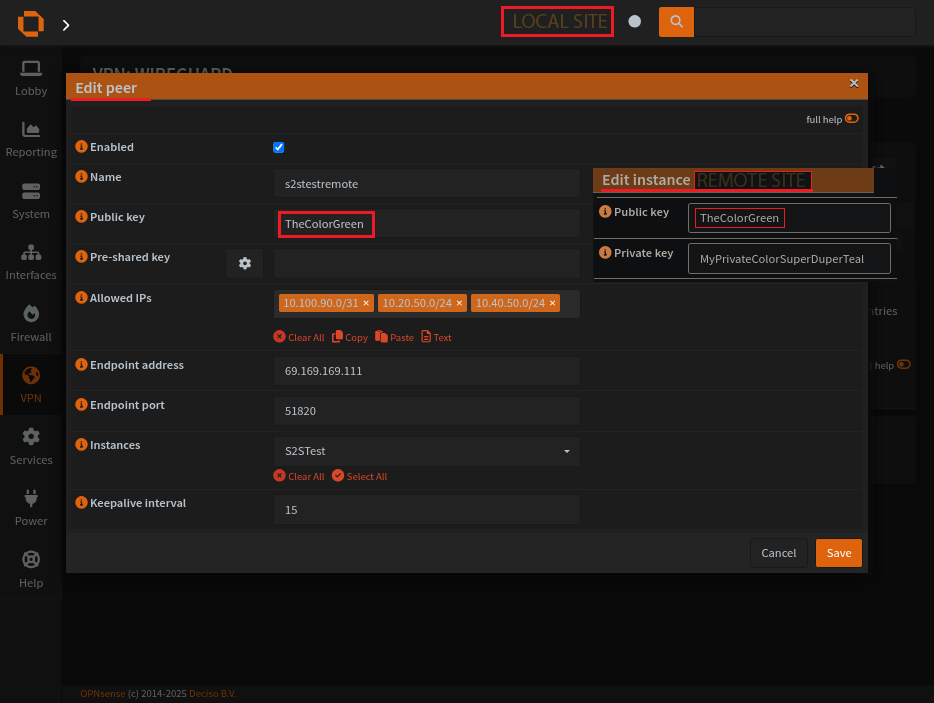
Create a wireguard instance
Demo how an instance is used by a peer to connect
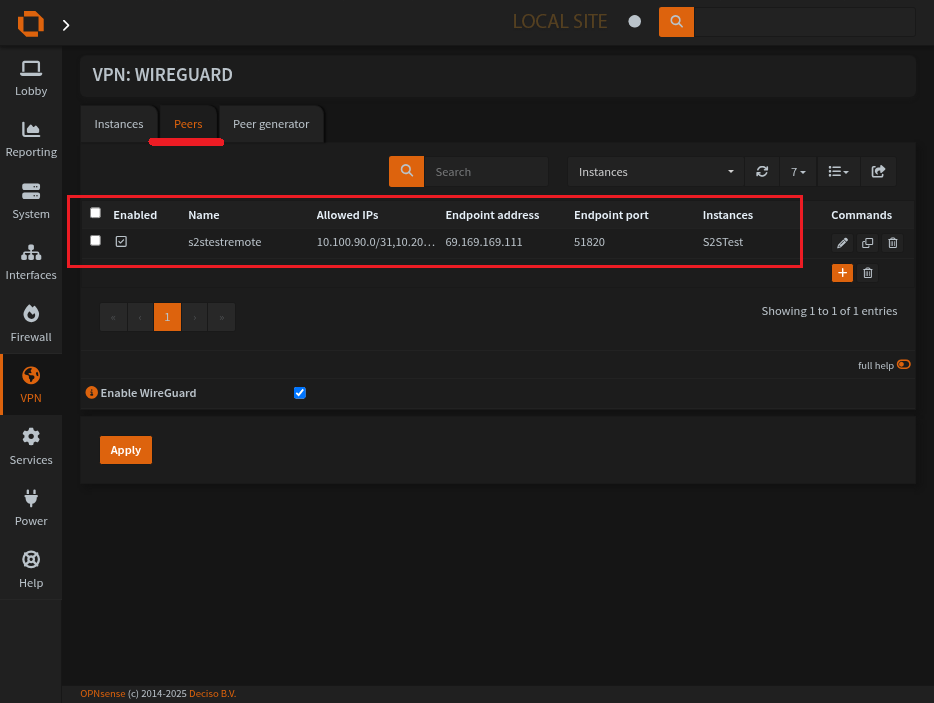
The wireguard peer page
Create a wireguard peer
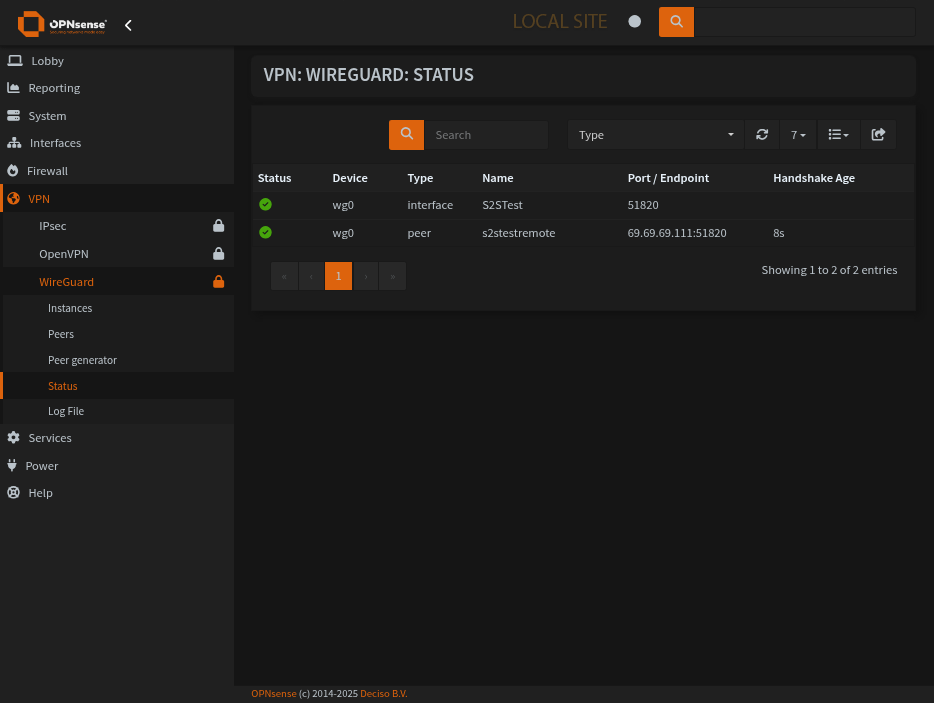
Looks like it works for me
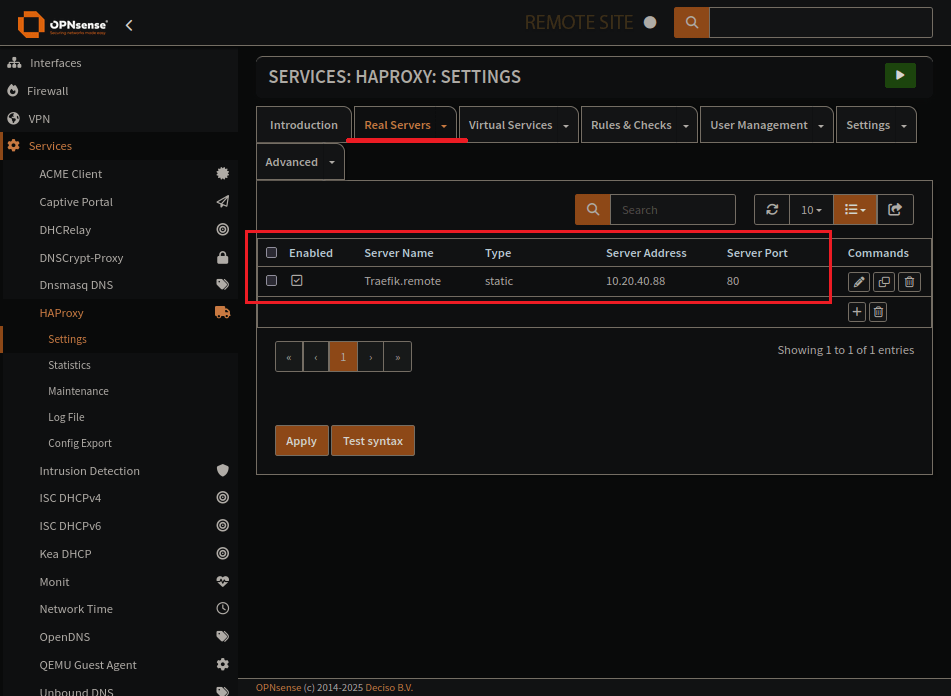
HAProxy
This is the reverse proxy.
Install HAProxy
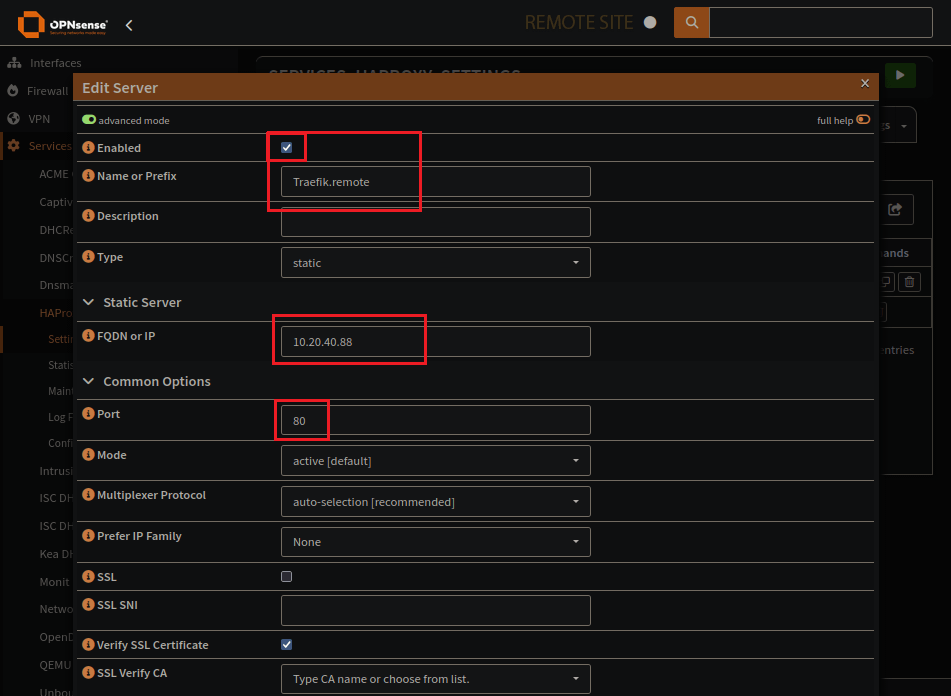
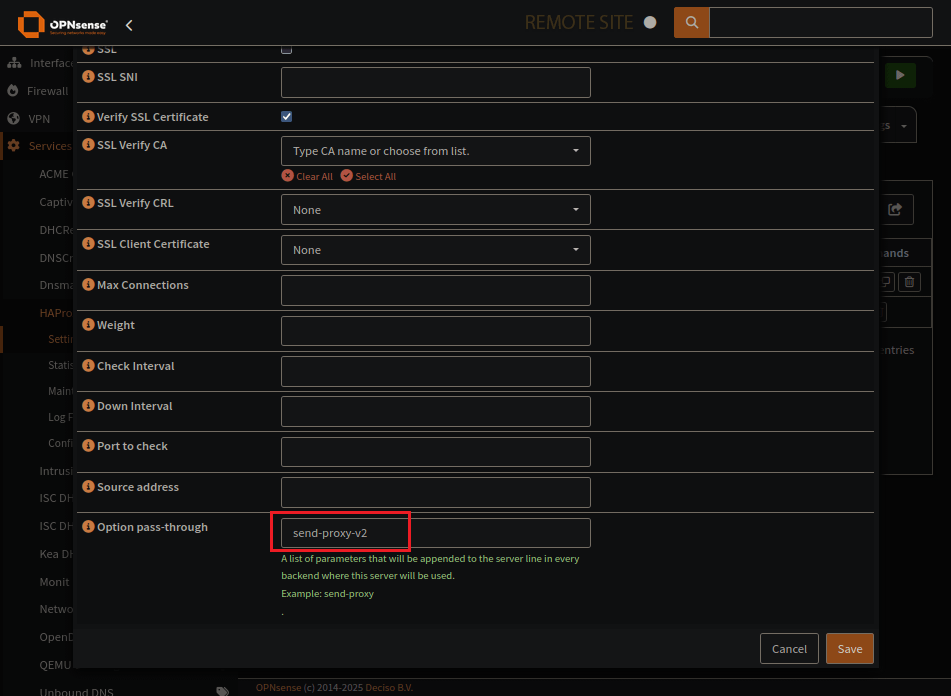
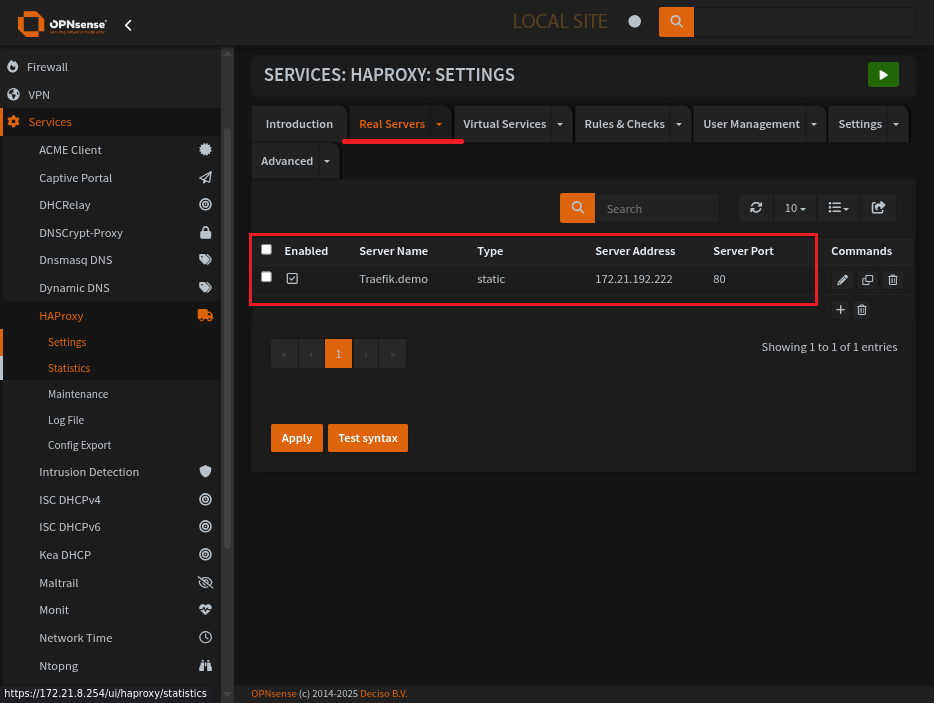
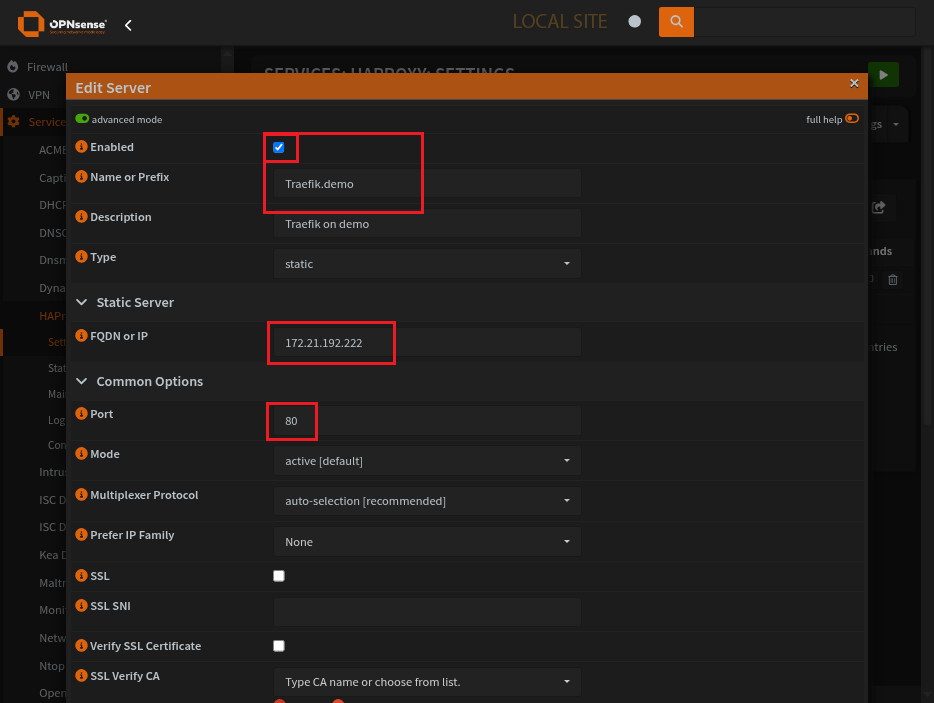
HAProxy Real Servers Page
The address of the server with Traefik on it, also the proxy-protocol version.
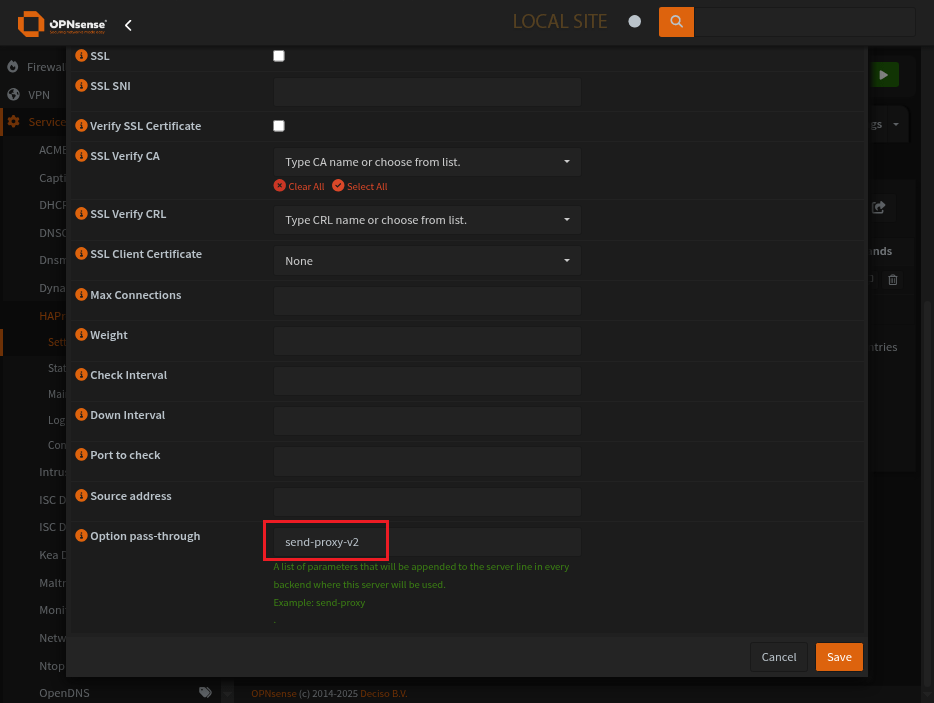
Be sure to send-proxy to the receving end
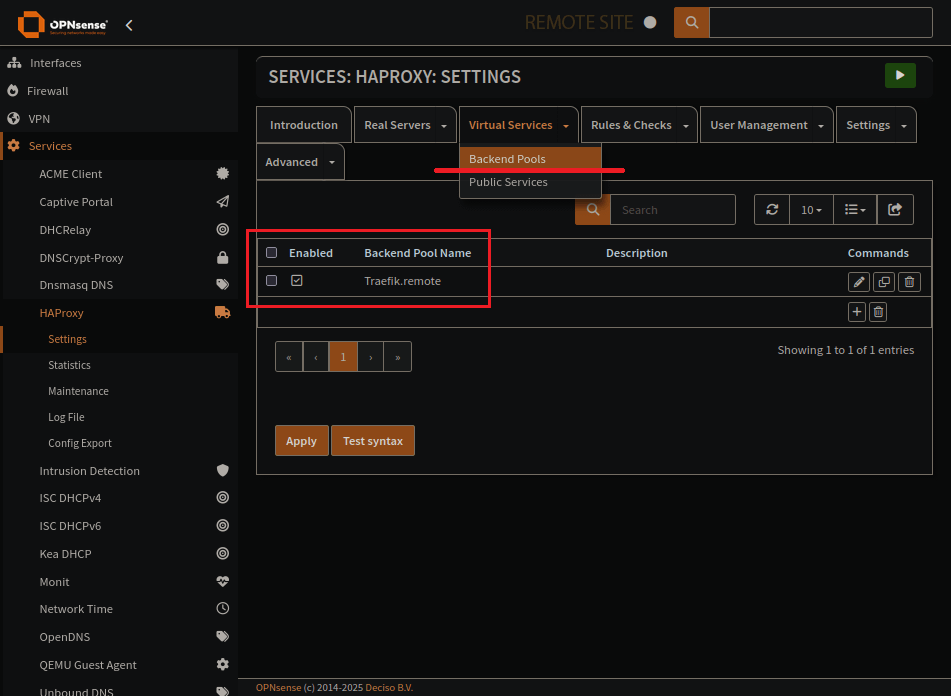
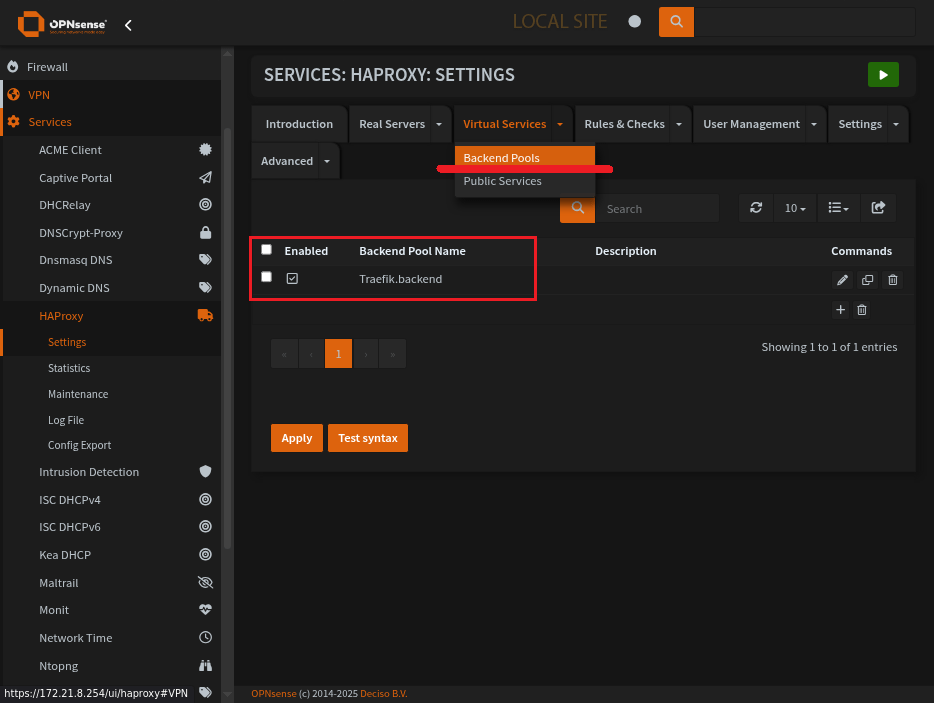
HAProxy Backend Pools Page
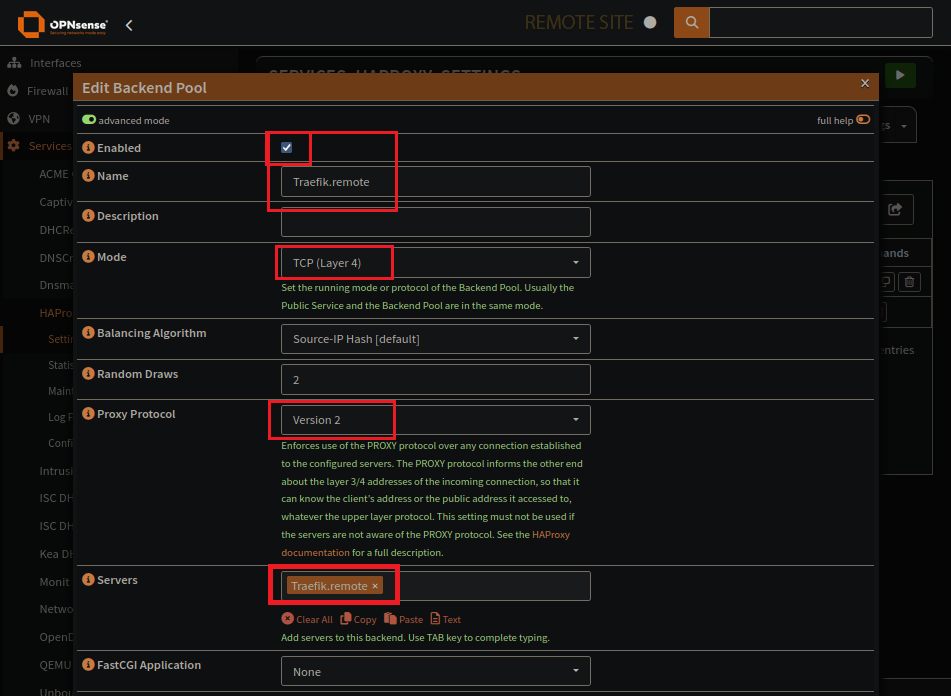
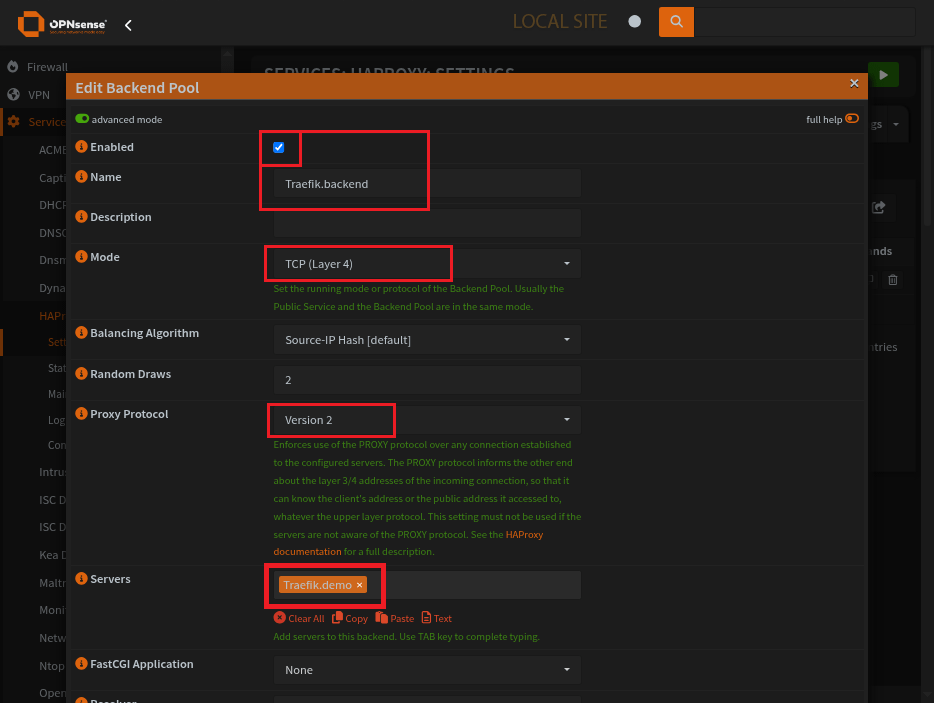
Backend pool creation
Backend pool specifies:
Protocol Mode: TCP
Proxy Protocol Version: 2
Real Servers to use:
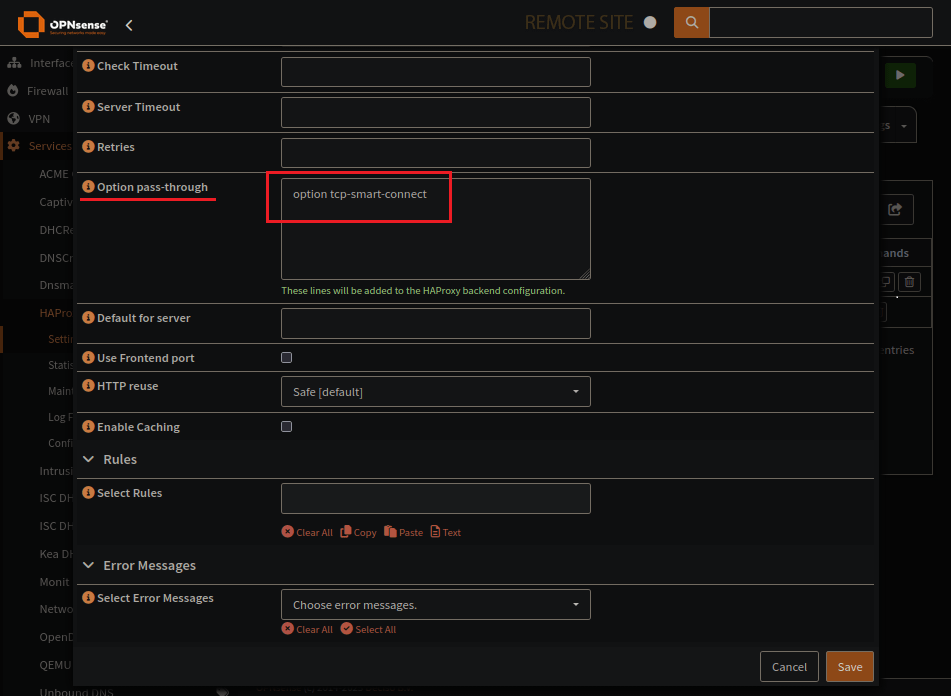
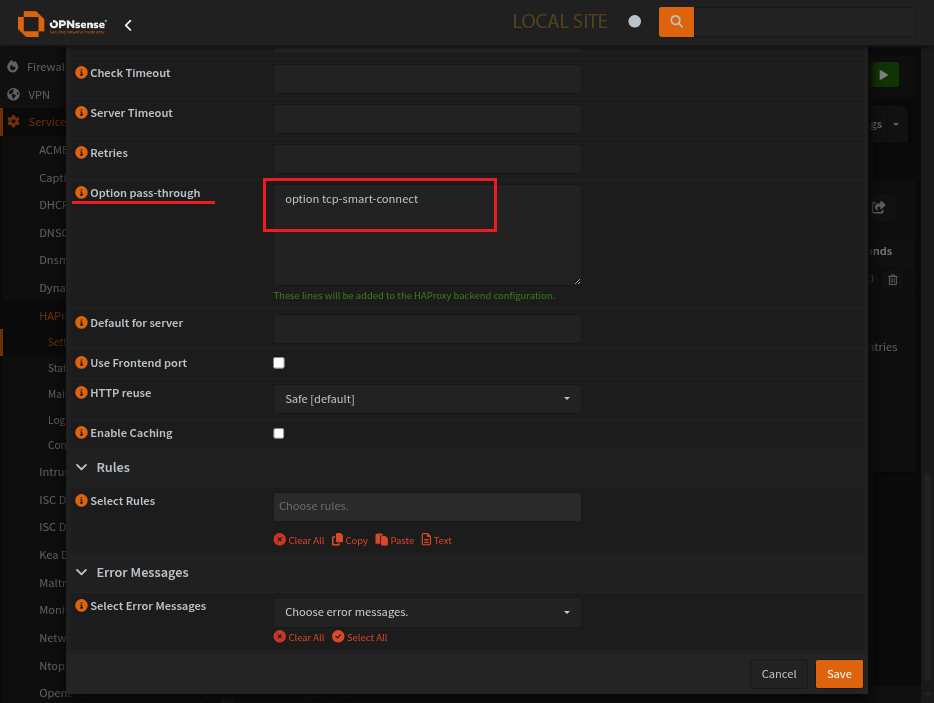
Options pass-through for config: option tcp-smart-connect
Options pass-through for config: option tcp-smart-connect
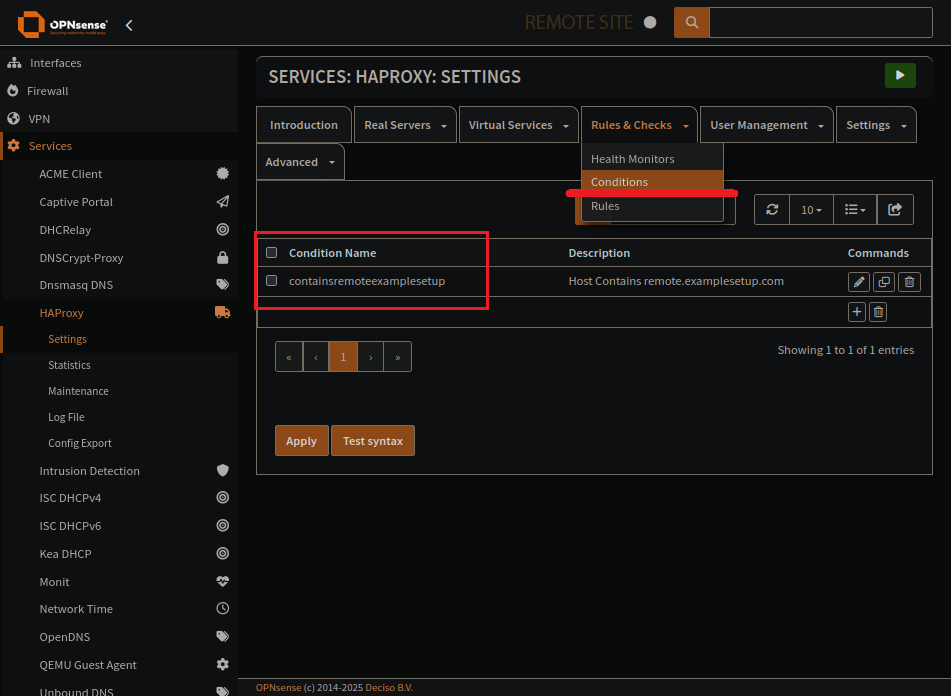
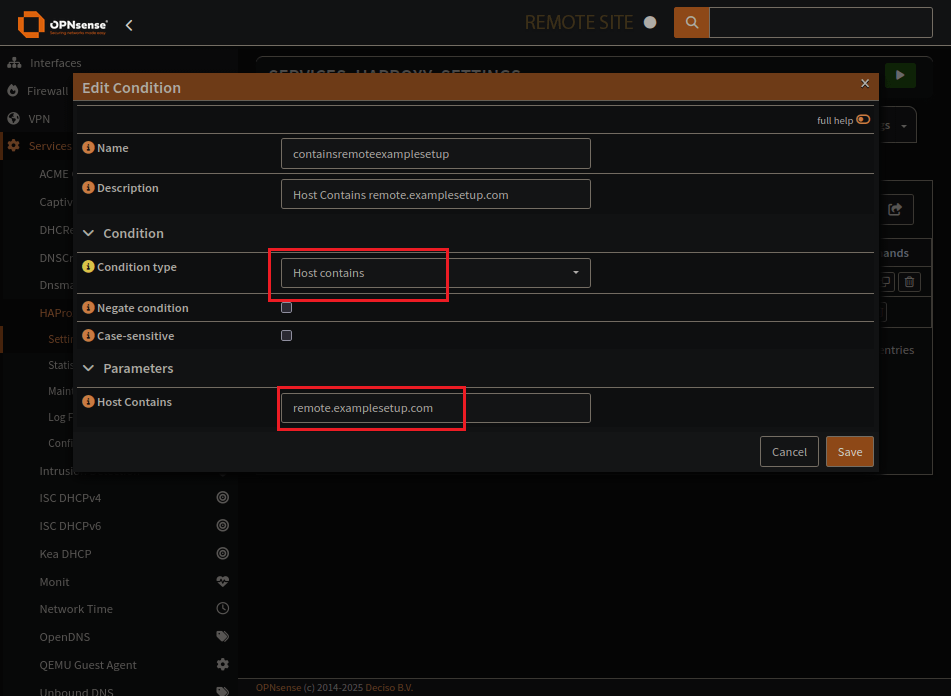
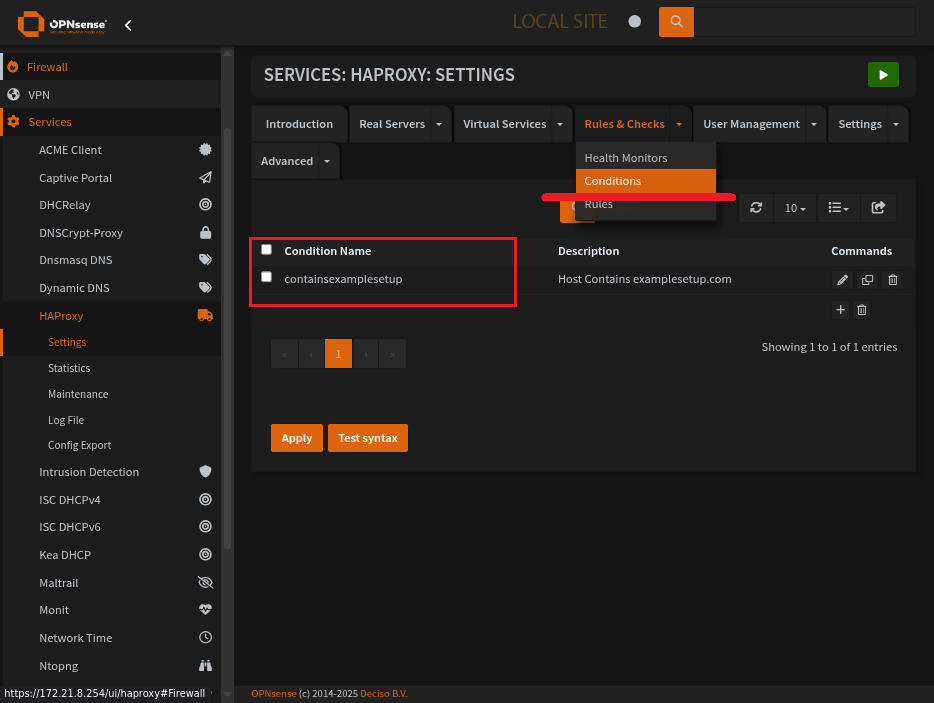
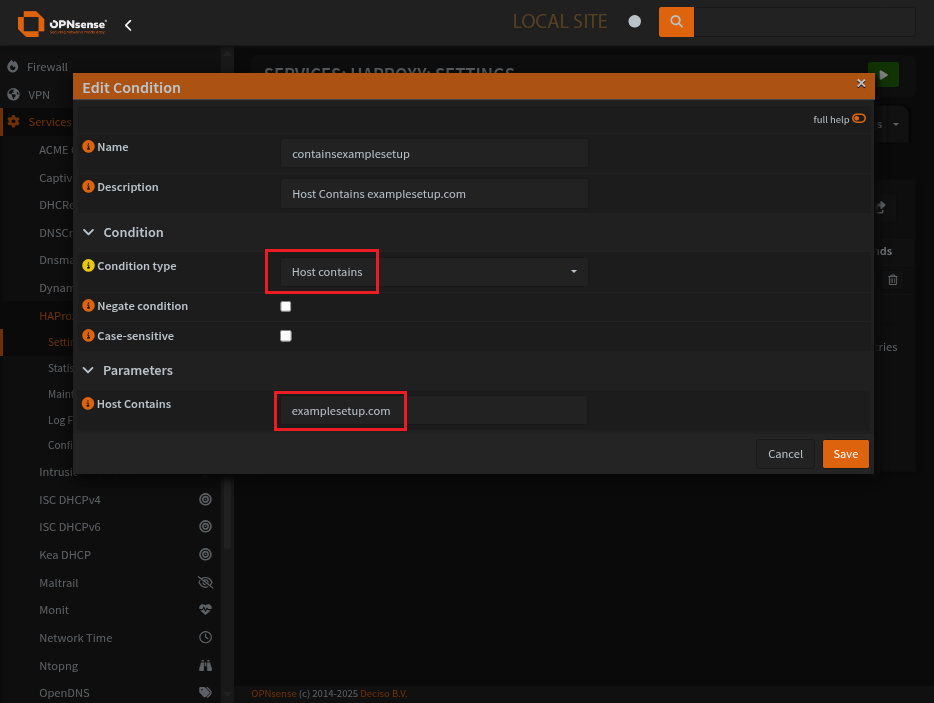
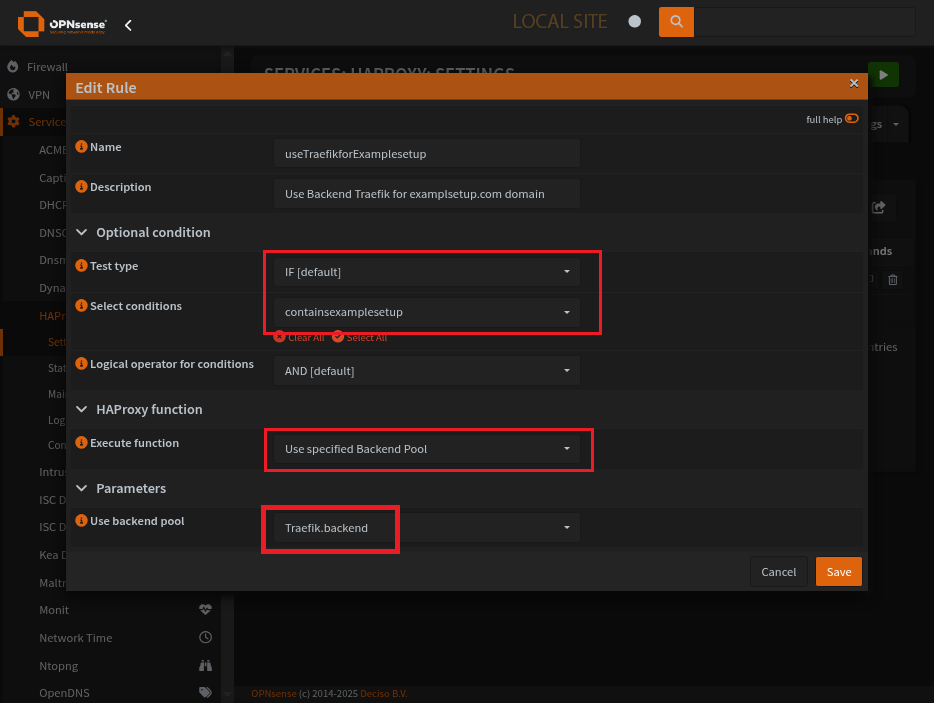
HAProxy Conditions Page
Condition sets the domain to look out for.
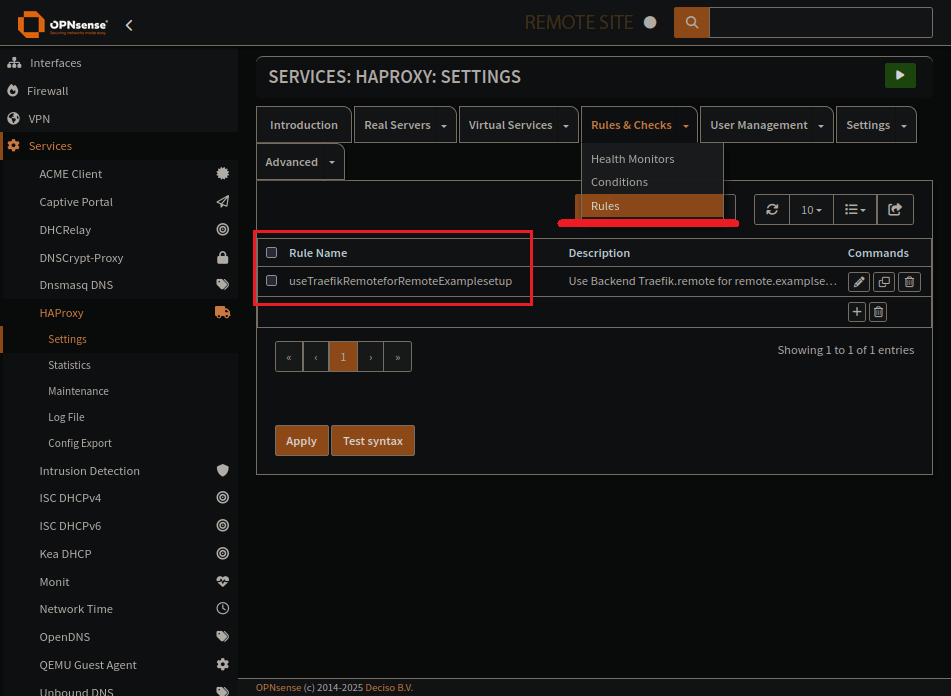
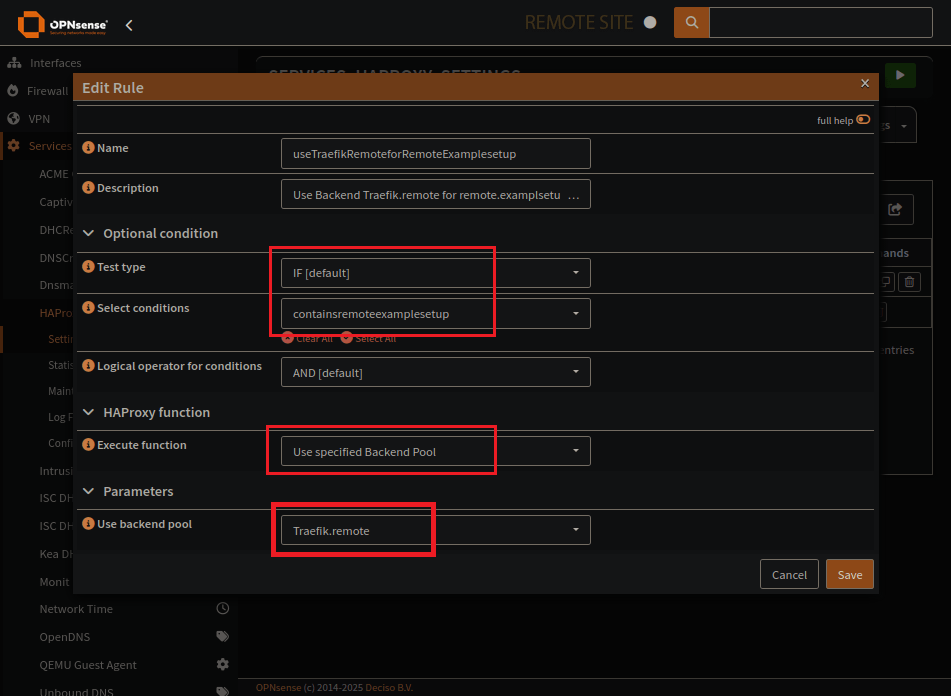
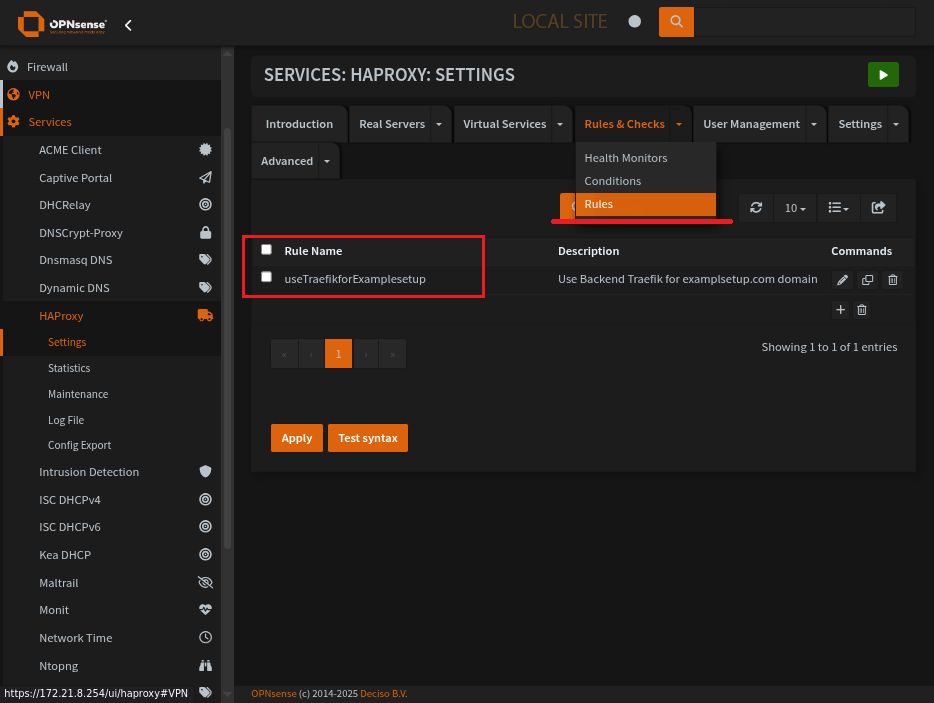
HAProxy Rules Page
Rule specifies what to do when your condition comes up. Use the correct pool for the subdomain.
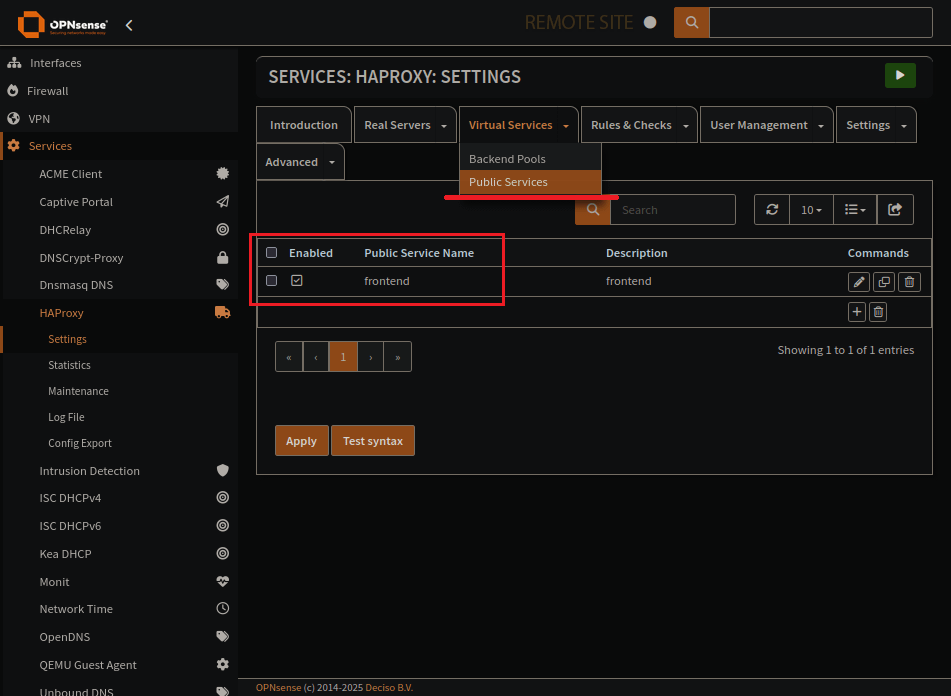
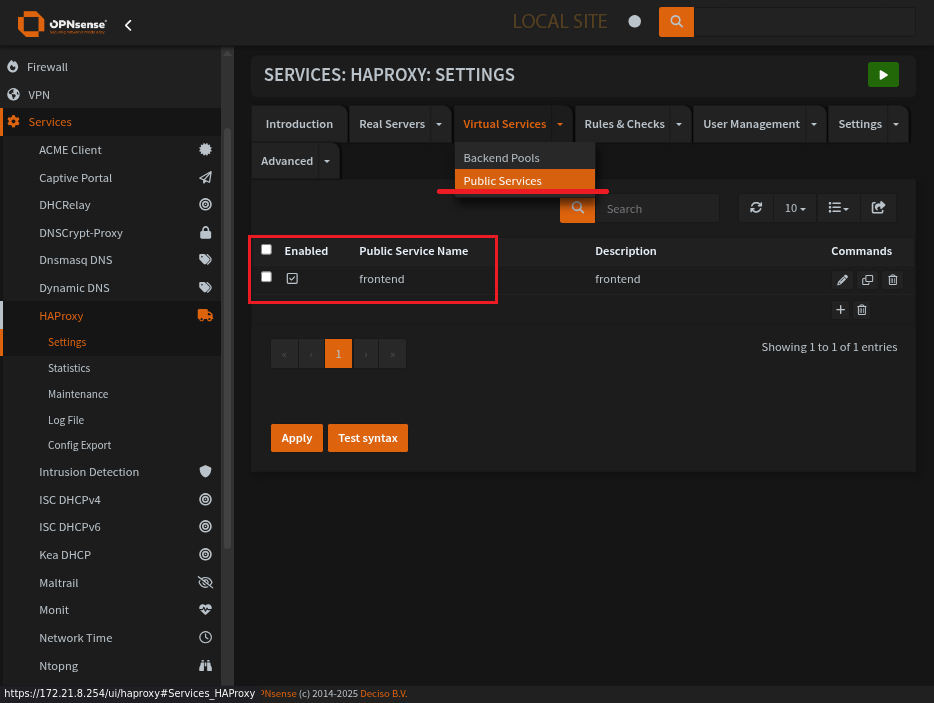
Here is the HAProxy frontend page, public servers
Frontend listen address and type
Frontend is what people connect to.
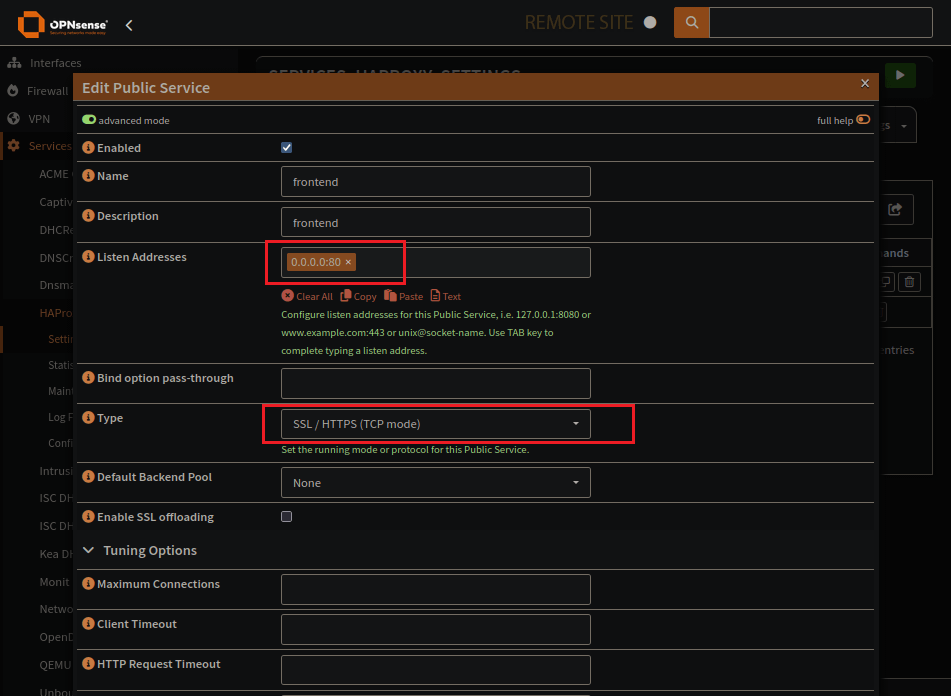
You need to set the address, and port, this could be a virtual IP.
You also need to be sure the:
Type: SS/HTTPS (TCP mode)
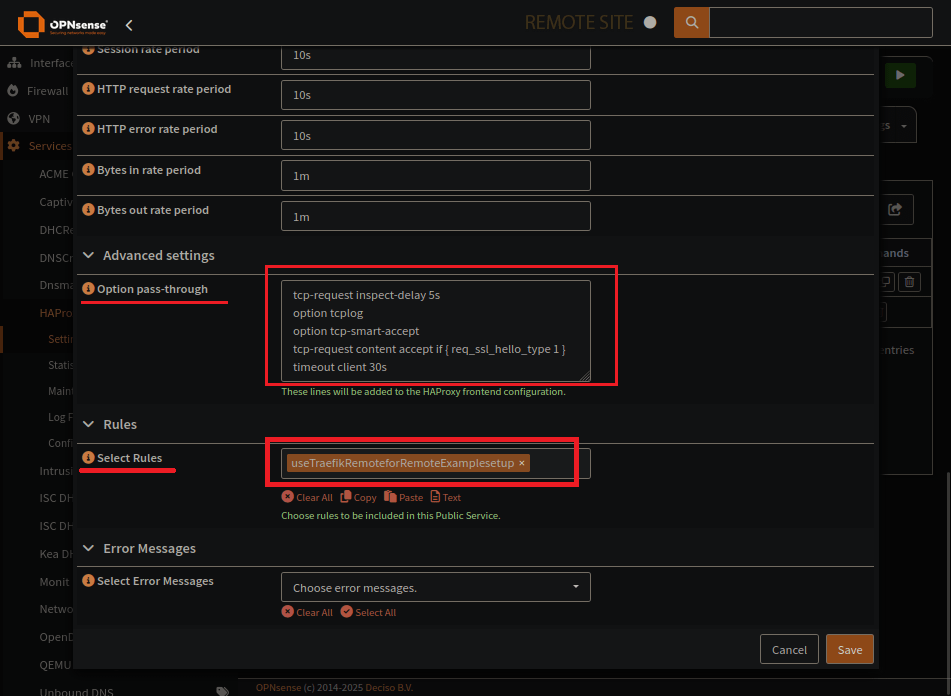
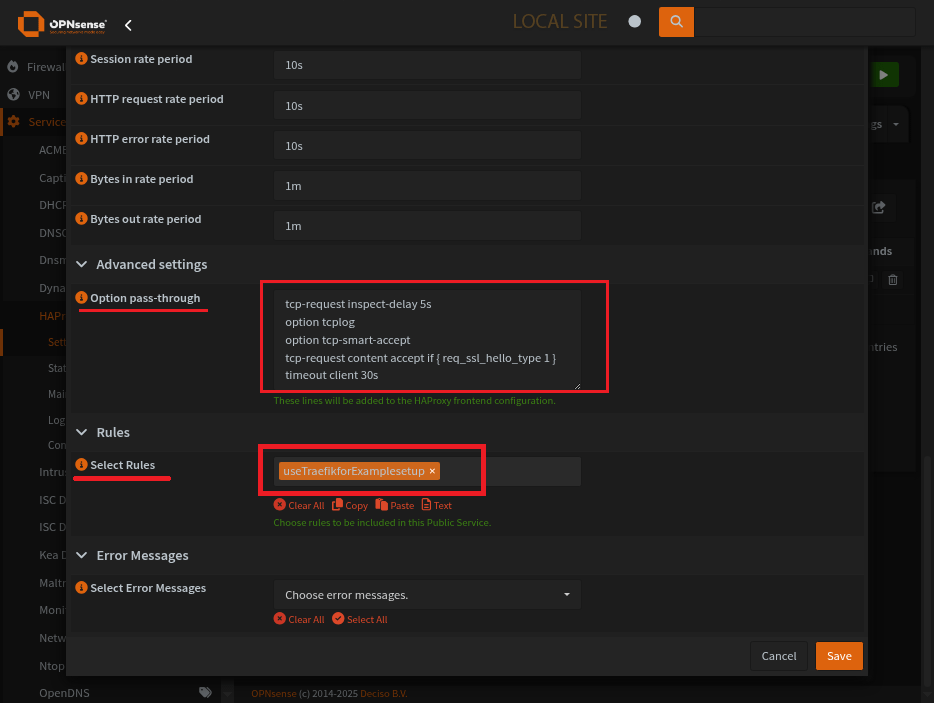
Advanced Settings:
There are a bulk of things to put here. They all help, but really you just need req_ssl_hello_type 1
Select Rules: Enter the rule tied to the backend for which this front end will go to.
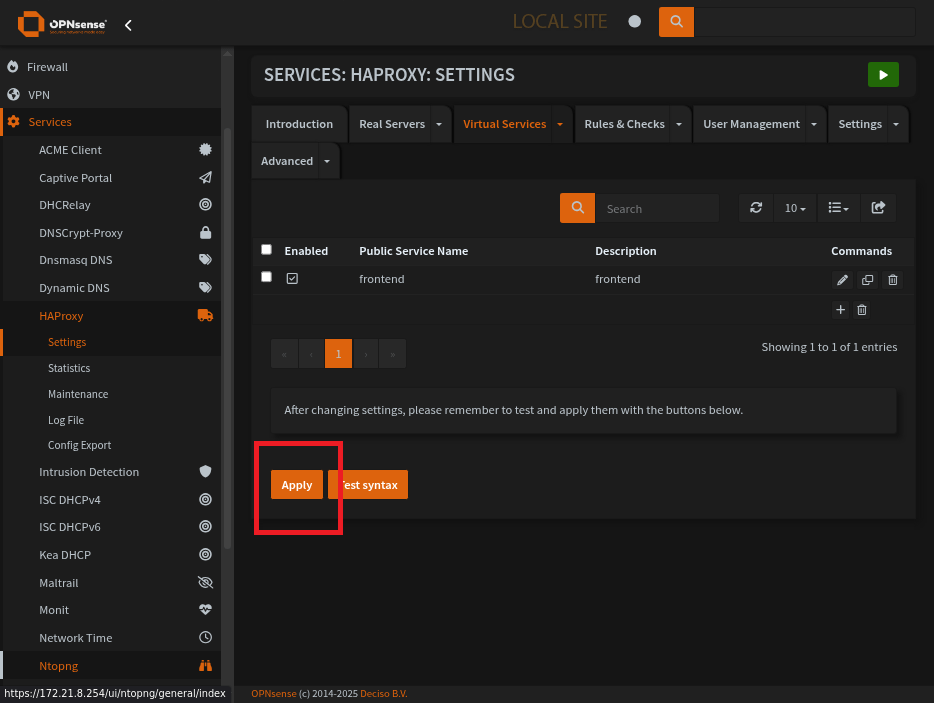
Save and Apply.